Organizations increasingly rely on their digital infrastructure to maintain business operations and continuity. In the rapidly evolving cybersecurity world, organizations need effective, dynamic security solutions to protect their most valuable assets.
October saw an unprecedented challenge for security teams as Vercara mitigated a record-setting Distributed Denial of Service (DDoS) attack that reached a staggering 1.4 Terabits-per-Second (Tbps) and 459.10 Million packets per second (Mpps). This attack shattered previous records of 1.2 Tbps and 420 Mpps, highlighting the growing scale and sophistication of cyber threats.
Digital infrastructure security insights and threat data continue to challenge security teams. For many organizations, mitigating Distributed Denial of Service (DDoS) attack risks is increasingly challenging, especially as the attacks become more complex and create a greater impact. Any service disruption that interrupts business operations or user access to services undermines an organization’s brand reputation and revenue.
This monthly roundup of reports provides information to help defenders manage their cloud-based security.
Every month, Vercara reports on trends across three critical infrastructure domains:
- Distributed Denial of Service (DDoS) attacks
- Domain Name Service (DNS) traffic
- Web Application Firewall (WAF) attacks
DDoS: Maintaining Steady Rates.
Overall, DDoS attacks saw a substantial 4.67% month-over-month increase. Of the data gathered, the following highlights offer insights:
- 14,829 DDoS attacks detected, with Vercara’s monitoring and mitigation preventing approximately 6,635 hours of downtime
- Port 23 (Telnet) is most frequently targeted port, indicating a potential tactic shift focused on exploiting legacy protocols
- Record-setting DDoS attack consisting of 1.4 Terabits-per-Second (Tbps) and 459.10 Mpps, surpassing previous records of 1.2 Tbps and 420 Mpps
Three factors drive these large-scale DDoS attacks:
- Proliferation of botnets
- Increasing reliance on Internet of Things (IoT) devices
- Cloud-based virtual private servers (VPS)
For more details on these attacks, check out the monthly DDoS Analysis Report.
Carpet Bombing Continues to Prevail.
In carpet bombing DDoS attacks, malicious actors target numerous IP addresses with smaller sized attacks to evade detection, making mitigation more difficult. Small attacks between 0-0.5 Gbps accounted for 92.22% of October DDoS attacks.
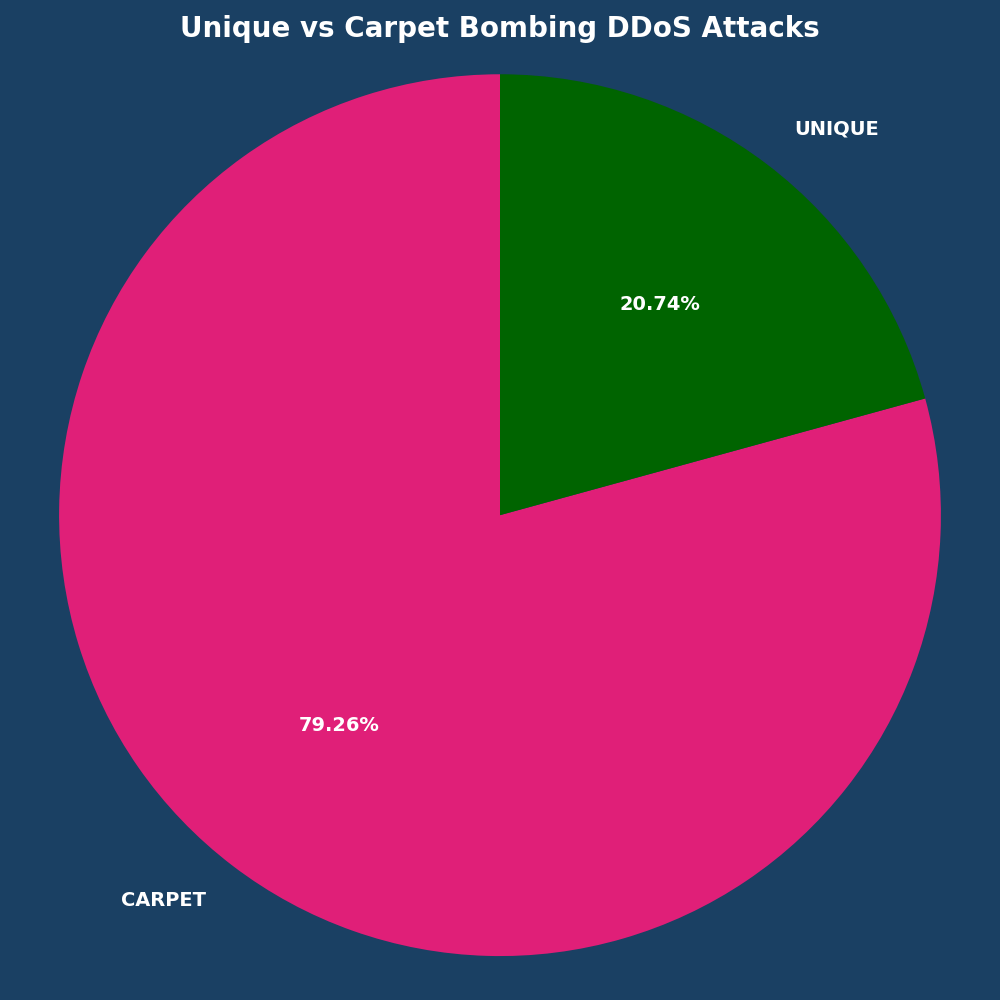
Carpet bombing attacks remain the primary threat, while mega attacks experienced their second month-over-month decrease in a row:
- Small attacks (0-0.5 Gbps): +11.73%
- Mega Attacks (100+ Gbps): -62.00%
| Gigabit-per-second | ||
| Gbps | Total Count | % |
| 0-0.5 | 12,192 | 92.22% |
| 0.5-1 | 1,235 | 8.33% |
| 1-5 | 857 | 5.78% |
| 5-10 | 235 | 1.58% |
| 10-50 | 248 | 1.67% |
| 50-100 | 43 | 0.29% |
| 100+ | 19 | 0.13% |
Since most organizations typically set alert triggers at higher gigabit levels, carpet bombing DDoS attacks create mitigation challenges because the threat actors:
- Remain under alerting thresholds
- Flood networks
- Rotate target IPs and destinations
- Rotate targeting methods and vectors
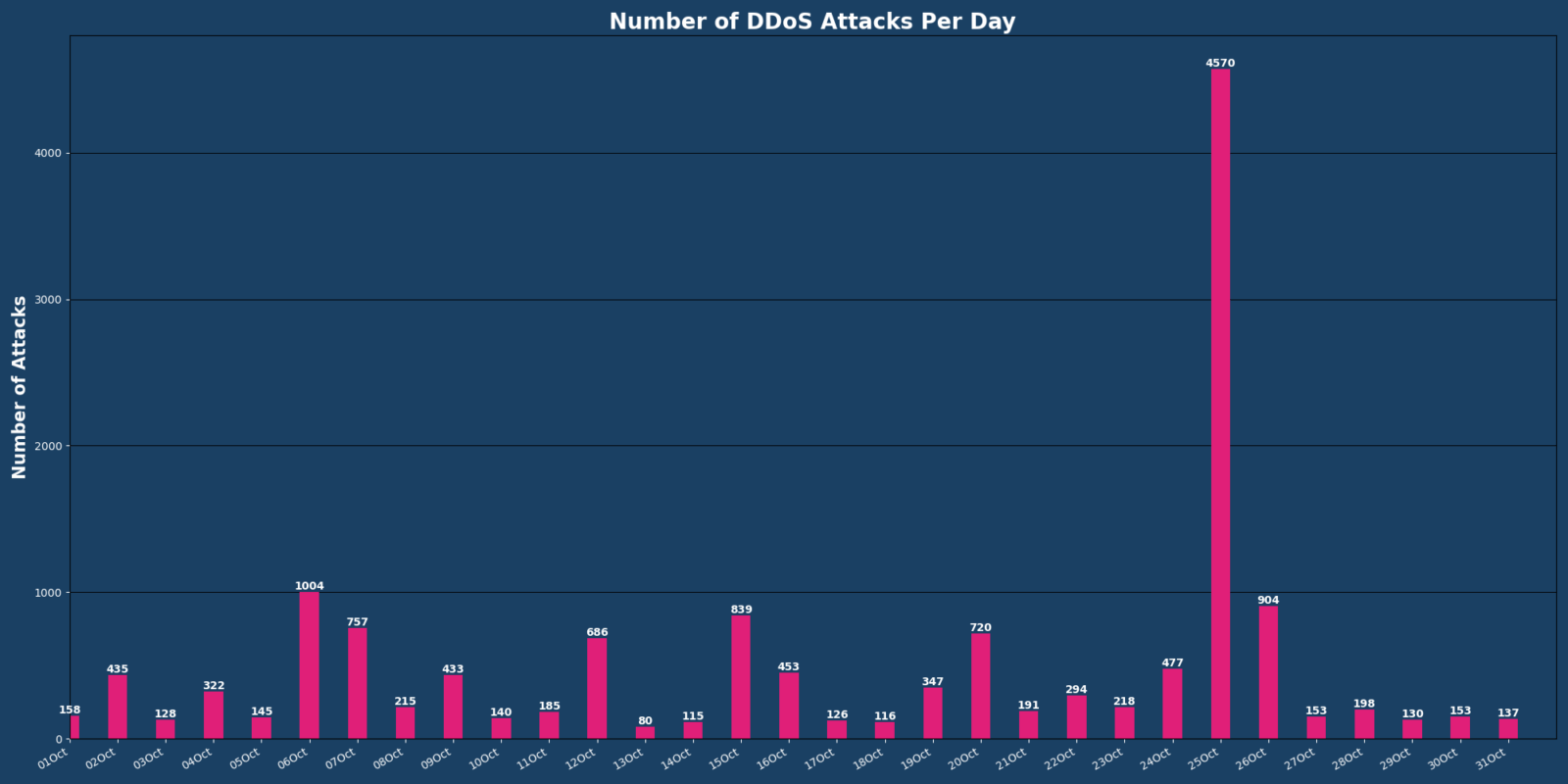
On October 25th, Vercara observed 4,570 DDoS attacks, an 824.54% increase from the daily average. Of those attacks, approximately 30% targeted a Communication Service Provider.
The longest carpet bombing attack occurred on October 25, consisting of around 2,609 small DDoS waves and lasting approximately 2 Hours and 32 Minutes. The second largest attack consisted of around 1,745 small DDoS waves and lasted around 4 hours and 26 minutes. The shortest attack lasted 23 minutes, occurring on October 16th.
Top 3 Attack Vectors Bring Some Surprises.
Total Traffic as an attack vector maintained its number one spot. Of note, Network Time Protocol (NTP), a vector rarely seen in the top ten, snagged second place. Finally, UDP moved to third place while TCP SYN/ACK Amplification came in fourth, replacing DNS Amplification, which only accounted for 2.6%6 this month. ICMP, which held third place in September, moved way down the line to ninth place.
The top four attack vectors for October were:
- Total Traffic: 37.11% (compared to September’s 28.10%)
- Network Time Protocol (NTP): 22.86%
- UDP: 12.23% (compared to September’s 17.9%)
- TCP SYN/ACK Amplification: 10.79%

The number of observed DDoS attacks consisting of one DDoS vector decreased from 76.42% in September to 70.89% in October.
Top 3 industries.
Financial Services remained the most targeted industry, with Software/Web Services and Communication Service Providers swapping places for the second month in a row. October’s top three industries by percentage of events were:
- Financial Services: 56% (compared to September’s 32.20%)
- Communication service providers: 23.69 (compared to September’s 18.22%)
- Software/Web Services: 4.64% (compared to September’s 28.13%)

DNS: Small Shifts Offer Larger Insights.
As a longer month compared to September, Vercara Managed DNS noted a 6.31% increase in overall web traffic for October. However, the daily queries remain statistically unchanged.

Vercara’s UltraDNS observed 101 DDoS attacks targeted against the platform in October, a decrease compared to September’s 157.

For more details on these attacks, check out the monthly DNS Analysis Report.
IPv4 and IPv6 Trends.
Overall, October followed in September’s footsteps with the Top 3 DNS Query types:
- A Record
- AAAA record (quad-A)
- Name Server (NS)
The consistent percentage of quad-A record queries indicates a continued shift toward IPv6 and its additional security benefits.
Notably, NSEC3PARAM record saw a 195.20% increase compared to September. DNS Security Extensions (DNSSEC) uses this record type to specify parameters to a resolver or authoritative DNS server, helping improve protections against zone enumeration while upleveling privacy by hashing domain record names.
DNS Response Codes Remain Statistically Stable.
The top two response codes remained the same month-over-month:
- “No Error”: most prevalent response code at 77.39%, a 6.76% month-over-month decrease
- “NXDomain”: 22.09%, a 4.60% month-over-month increase
The NXDomain response code can indicate a misconfiguration or attackers using DNS enumeration tools that can cause a DDoS attack.
Industry Sectors.
Industry sectors continue to work on and improve their DNS management, with October’s report showing both wins and areas for improvement.
Generally, the DNS record-type queries provide insight into how the industry uses digital infrastructure. Some highlights include:
- Widespread requests for HTTPS records indicate an emphasis on secure web communications.
- Gaming and Gambling focus on MS records indicates the importance of reliable email communications.
Software/Web Services and IT/Technical Services.
These two industries received the most DNS queries, representing 79.04% of all DNS queries. The number indicates the sectors’ extensive reliance on robust DNS services for:
- Web hosting
- Cloud services
- Technical operations
Additionally, the Software/Web Services industry had a significant presence of ‘No Error’ responses, indicating effective DNS management.
Administrative Services and Construction.
Across these two industries, the most prominent response code returned is the NXDomain. These high rates suggest a need for improved domain management practices and security measures.

Web Application Firewall (WAF): Back to Reality.
During October, Vercara UltraWAF processed over 595 million web requests, a slight decrease compared to September. Of these requests, 16.97% were malicious and 2.28% were identified as bot traffic.
Notably, XML WSI Error Body Environment Namespace category experiences a 3,100% increase, indicating that attackers may be trying to exploit potential XML structure issues for attacks like:
- XML injections
- Denial-of-Service (DoS)
- WAF bypassing
- XML External Entity (XXE) attacks
For more details on these attacks, check out the monthly WAF Analysis Report.
Up and Down.
October’s data found:
- 26.62% increase in malicious activity compared to September
- 17.84% decrease in the amount of bot traffic compared to September

Same Top 3.
Along with these overall increases, October showed additional changes:
- Cookie threat category remained most prevalent, accounting for 44.09% of malicious traffic
- Command Injection came in second, accounting for 28.47% of malicious traffic
- Invalid RFC threat came in third, accounting for 13.68% of malicious traffic

October Countermeasure of the Month.
This month, our featured countermeasure is the Transport Layer Security (TLS) (formerly Secure Sockets Layer, or SSL) options built into UltraWAF’s asset configuration wizard. These options allow administrators to set up front-end TLS to communicate with the browser and back-end TLS to communicate with their application server.
The minimum TLS version is a simple drop-down selector. Most websites should select TLS 1.2, which also includes TLS 1.3. Choose only a lower version if you are concerned about older, legacy web browsers.
HTTP Strict Transport Security (HSTS) is a policy that sets HTTP headers so that browsers know to only come to the TLS-protected (i.e., HTTPS) version of the site in the future. This should be enabled if the application server does not send HSTS headers.
Turnkey Cloud-based Security with Vercara.
Vercara provides a turnkey, multilayered approach to security with UltraDNS, UltraDDoS, and UltraWAF. With Vercara’s comprehensive suite of solutions, organizations gain advanced security capabilities, insights for informed decision-making, and improved resilience against cyber threats.
To learn how Vercara’s suite of solutions can help defend your organization, contact our sales team.


