Since the beginning of computer networking and the birth of the Internet, Distributed Denial of Service (DDoS) attacks have remained a persistent threat. These attacks often leverage various techniques to overwhelm the network circuits, routers, and applications of a targeted organization. Among these different techniques, manipulation of Transmission Control Protocol (TCP) flags stands as a potent method, misusing and abusing the TCP protocol to disrupt services and impair network functionality. The first recognized DDoS attack in 1996 was conducted by manipulating TCP flags, specifically a TCP SYN flood attack.
What are TCP flags?
The TCP protocol governs the reliable transmission of data across networks, employing a series of control flags to manage communication sessions. These flags include SYN (Synchronize), ACK (Acknowledgement), RST (Reset), FIN (Finish), and others, each serving a distinct function within the TCP handshake process and data transfer protocols.
A TCP connection is initiated by what is called the “TCP Three-Way Handshake” to establish a reliable connection. The initiating client sends an SYN packet to the destination server, which in turn sends an SYN/ACK packet back to the client, and finally, the client sends an ACK packet back to the server. Once this handshake is done, the two endpoints negotiate the connection’s parameters before transmitting data, such as an HTTP request.
![]()
Exploiting TCP flags in a DDoS attack.
Malicious actors exploit the inherent flexibility of TCP flags to inundate a targeted system with malicious traffic, thereby disrupting services and causing network outages. Because a malicious actor does not need to establish the TCP three-way handshake, they can flood their target with packets from random spoofed source IP addresses, making it harder to mitigate this type of cyberattack. Malicious actors can orchestrate a variety of DDoS attacks by altering TCP flag combinations such as SYN. Floods, ACK Floods, and RST/SYN-ACK Floods.
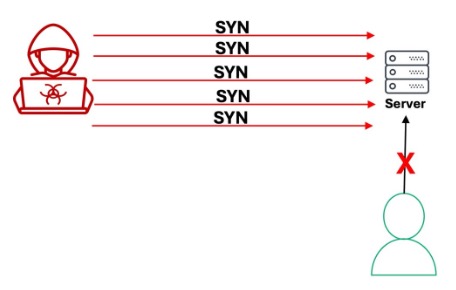
SYN Floods: In a SYN flood DDoS attack, malicious actors send a significant number of SYN packets to a target server with the intention of exhausting resources by establishing multiple half-open connections without completing the TCP three-way handshake process. The flood of SYN packets overwhelms the capacity of the network, routers, and servers to handle incoming connection requests, rendering them unable to respond to legitimate users.
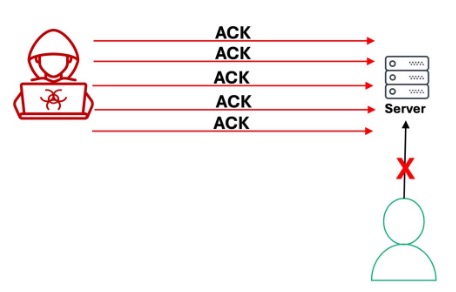
ACK Floods: in an ACK flood DDoS attack, a malicious actor sends an excess of ACK packets to overwhelm and consume all available resources such as CPU, memory, and network bandwidth, thereby causing the targeted system to become unresponsive to legitimate requests.
RST/SYN-ACK Floods: Malicious actors can also employ RST and SYN-ACK flags to disrupt communication between network hosts. By sending spoofed RST or SYN-ACK packets to terminate or manipulate established connection, malicious actors can disrupt service availability.
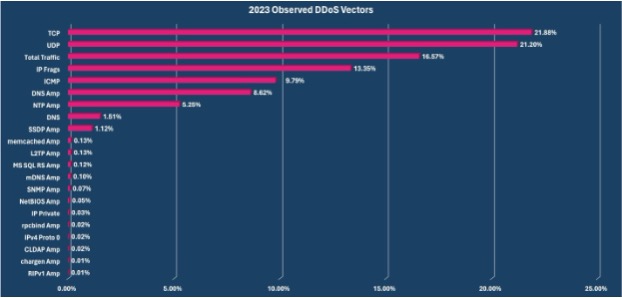
Vercara has seen this trend in the DDoS attacks directed against our customers. During 2023, Vercara observed 27,253 occurrences of malicious actors utilizing some form of TCP flag manipulation, accounting for over 21% of all observed DDoS vectors, and was able to mitigate this style of DDoS attacks with little to no disruption or degradation to our customer’s online presence.
Impacts of TCP DDoS attacks.
The ramifications of DDoS attacks leveraging TCP flags can be very significant, causing immediate disruption and long-term consequences:
Service Disruption: DDoS attacks utilizing TCP flags can result in significant service disruption, causing websites to become inaccessible, applications to malfunction and critical network infrastructure to fail.
Financial Losses: Organizations targeted by DDoS attacks may incur substantial financial losses due to downtime, decreased productivity, and potential damage to their reputation and customer trust.
Data Breaches: In some cases, DDoS attacks serve as an attempt to overload incident response teams so that the attackers can conduct more sinister cyber-attacks, such as data breaches or network intrusions, exacerbating the impact and extending the scope of damage.
Legal and Regulatory Ramifications: In certain industries, such as finance, healthcare, and e-commerce, prolonged service disruptions resulting from DDoS attacks may violate regulatory requirements and contractual obligations. Organizations failing to meet service level agreements (SLAs) or compliance standards may face legal consequences, including fines, litigation, and regulatory sanctions.
Mitigation strategies.
To mitigate the risk of DDoS attacks leveraging TCP flags, organizations can adopt a multi-layered security approach, incorporating proactive measures and robust defensive mechanisms:
- Utilizing a cloud-based DDoS mitigation service: These specialized services offer comprehensive protection against DDoS attacks, such as DNS amplification, and can handle these large attacks. They employ advanced filtering techniques and can absorb large traffic spikes upstream from the target network.
- Use cloud-based WAFs and CDNs: Leverage Content Delivery Networks (CDNs) and Cloud Web Application Firewalls (WAFs) to distribute network traffic across geographically dispersed servers, reducing the likelihood of service disruption and enhancing resilience against DDoS attacks.
- Network Monitoring: Implement comprehensive network monitoring solutions capable of detecting abnormal traffic patterns and flagging potential DDoS attacks in real time.
- Traffic Filtering: Employ ingress and egress traffic filtering techniques to identify and block malicious packets at the network perimeter, thereby mitigating the impact of DDoS attacks before they reach critical systems.
- Rate Limiting: Implement rate-limiting measures to restrict the volume of incoming connection requests, preventing SYN flood attacks from overwhelming server resources.
- Anomaly Detection: Deploy anomaly detection systems capable of identifying unusual TCP flag combinations and anomalous network behavior, enabling timely or automated response and mitigation.
Bolster your defenses.
DDoS attacks leveraging TCP flags represent a formidable threat to network infrastructure and service availability, exploiting vulnerabilities in the TCP protocol to disrupt communication and impair system functionality. By understanding the mechanics of these attacks and implementing strong mitigation strategies, organizations can bolster their defenses against DDoS threats, safeguarding their networks and preserving operational continuity in the face of adversity.