In February, we released UltraDDR, a filtering recursive DNS resolver service powered by a massive amount of historical and near-term DNS data. This is what we refer to as the “Adversarial Data Lake”. With over ten years of historical data, we look at domain age, the trustworthiness of the registrar, if the IP address for a record was used previously for malware command and control (C2), if the domain has been dormant for a long time and has recently “woken up,” and other indicators that the domain may be suspicious or malicious.
UltraDDR uses this data to categorize domains and hostnames. The first time a Fully Qualified Domain Name, or FQDN, is queried through UltraDDR, it puts that FQDN into the Watch Engine and sets its visible status in the portal to “Watch Engine”. The Watch Engine examines the correlation with historical data and updates as more usage patterns are observed. If an FQDN is determined to be suspicious, its status is upgraded to “Highly Suspicious”. And finally, if it has been confirmed to be malicious, we start blocking it.
For your typical Cyber Threat Analyst, the Adversarial Data Lake is a goldmine for threat hunting, and this data is exposed via the UltraDDR portal interface.
Threat hunting is the process of using your data sources to find malicious activity that is not immediately detected and blocked by your tools. This can help to tune your tools such as SIEM, IDS, firewalls, etc. It can also help you to identify additional malicious activity associated with the activity that is detected.
UltraDDR does an excellent job explaining how and why a particular hostname is categorized. For example, in this screenshot from the FQDN ehl6yjjehl6.setandforget.com, both the domain (setandforget.xyz) and the Top-Level Domain (.xyz) are not trusted due to heavy abuse coming from them.

You have the ability to explicitly block this FQDN as a “manual override”, and you can also tag and make notes on each FQDN and domain. That way, the next Cyber Threat Analyst can learn from your work.
There are four different ways that you can use UltraDDR’s portal for threat hunting using the built-in filter, sort, and aggregate features. Inside the portal, you can select which fields are visible in what order and sort by any of these fields. The default view is to show Blocked, Highly Suspicious, and Watch Engine traffic.
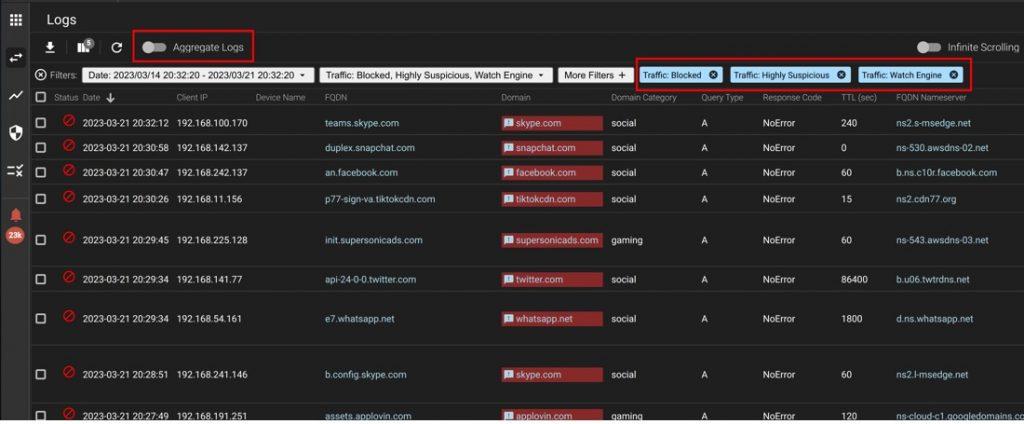
Long tail domains.
The first technique that you can use for threat hunting is to look for the “long tail”: domains that get a small number of queries. Most of the queries against a recursive DNS resolver will be for the popular domains. So, if you remove all that noise from the query logs, you can look at the long-tail domains which is where a lot of the interesting malicious activities are.
To get this view, you can use the “Aggregate Logs” button. That gives you the count of queries by domain.
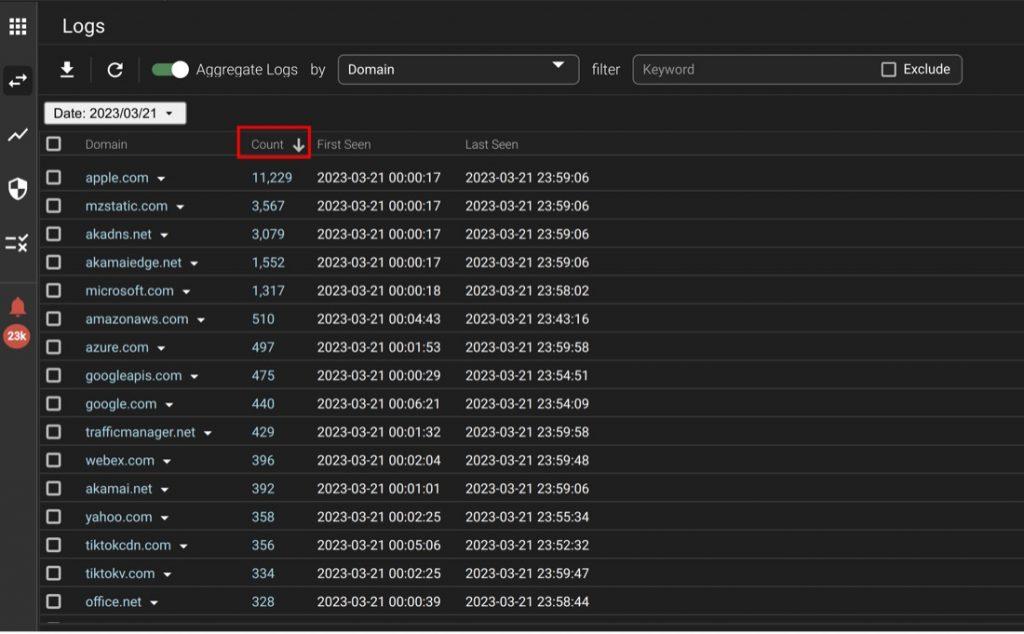
You see the obvious high-query domains here. But if you click on the “count,” column header, it reverses the order, and you now see the low-queried domains first. You can click on any domain to see its details and to explicitly block it.
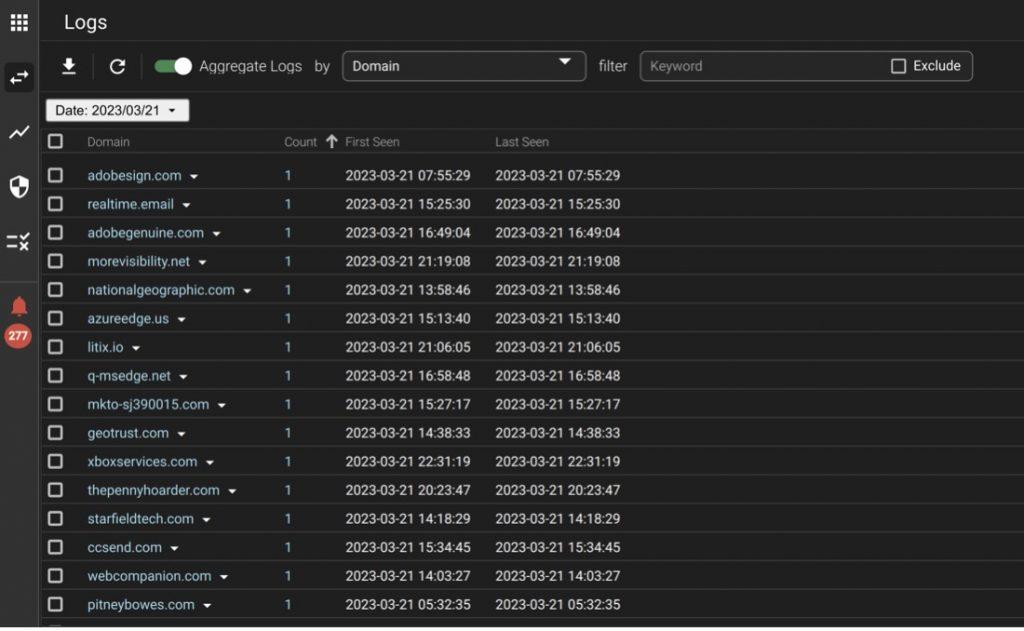
Using the Watch Engine.
The second view that you can use is to show domains that are being decided on by the Watch Engine. These things are under investigation and might be blocked in the future. This typically will be the brand-new FQDNs and domains. To get this view, I remove the filter that shows me the blocked domains and add a negative filter for categories and blocked traffic. Categories are pre-populated lists that are used to enforce Acceptable Use Policies, such as keeping users from visiting social media and sports sites using company IT assets. Filtering these out of the logs is a quick process. Add a filter for “Domain Category,” hit the “Select All” button, the “Excludes Keyword,” and apply the filter.
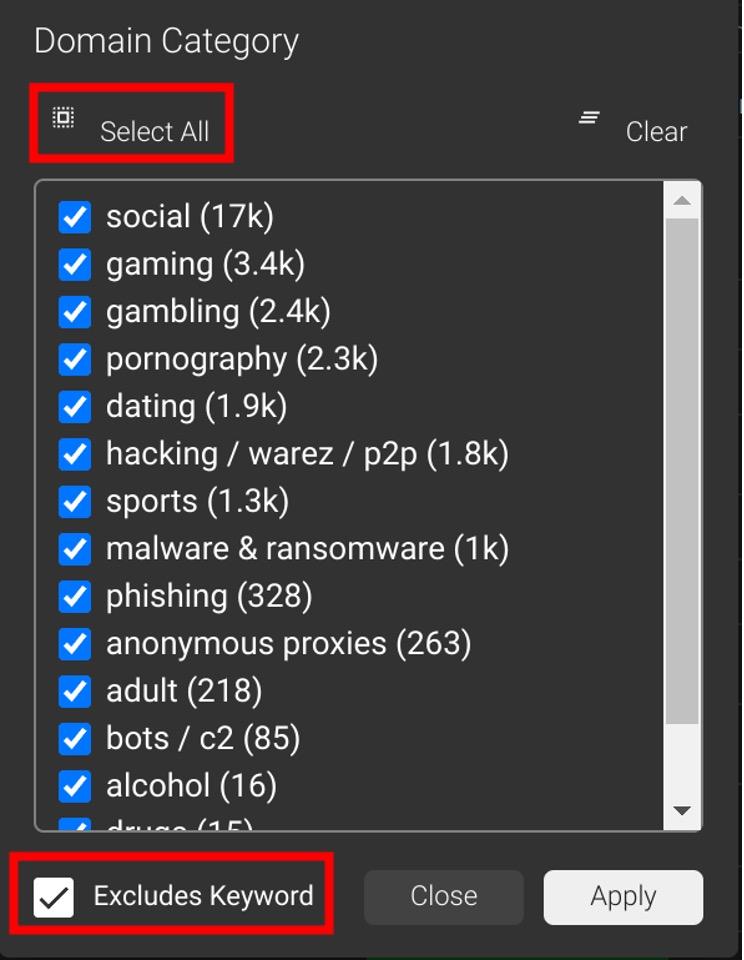
Then to filter out the blocked traffic, pick the “Traffic” quick filter and set it to just show “Highly Suspicious” and “Watch Engine” traffic.
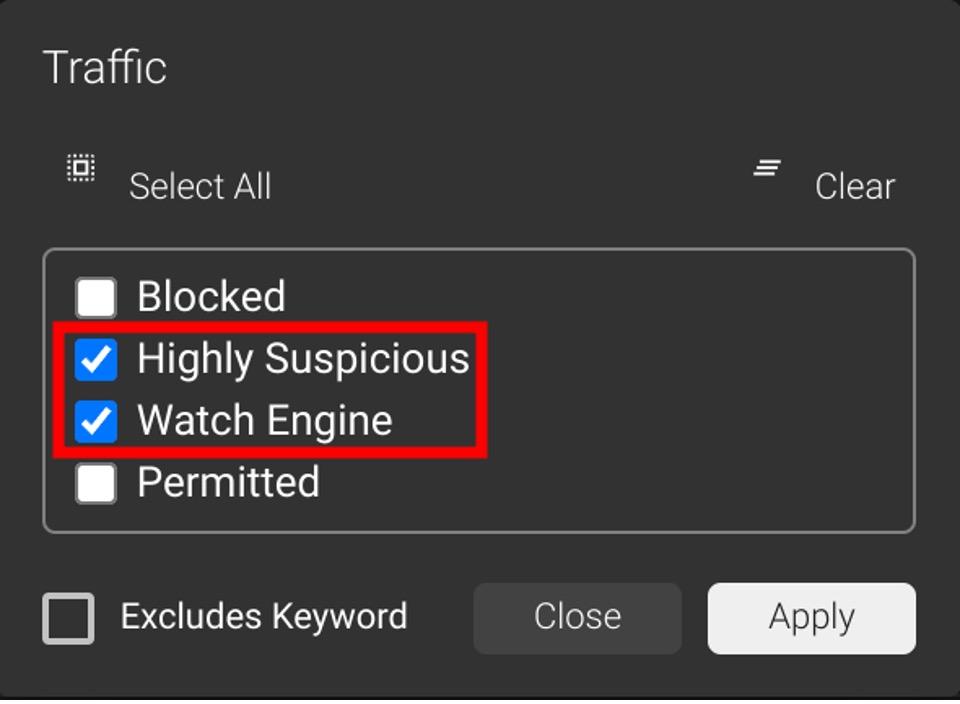
This should give you the following view:
Using Indicators of Compromise from threat intelligence.
The third way to use UltraDDR for threat hunting is to check it against a list of known malicious domains. For example, in March, we received this advisory from CISA on the Royal ransomware family that contains Indicators of Compromise (IoC), typically FQDNs, domains, or individual IP addresses.
Inside our CTI team, when we get data like this, we have two objectives that we want to achieve. The first one is to see if these domains are being blocked by UltraDDR and, if not, to seed them into the Watch Engine for categorization to get them blocked. This is easy enough to do —end a DNS query to UltraDDR for each FQDN or domain. We use a simple script to iterate through each list and send a query.
Then the second objective is to identify if any of your computers have gone to those.
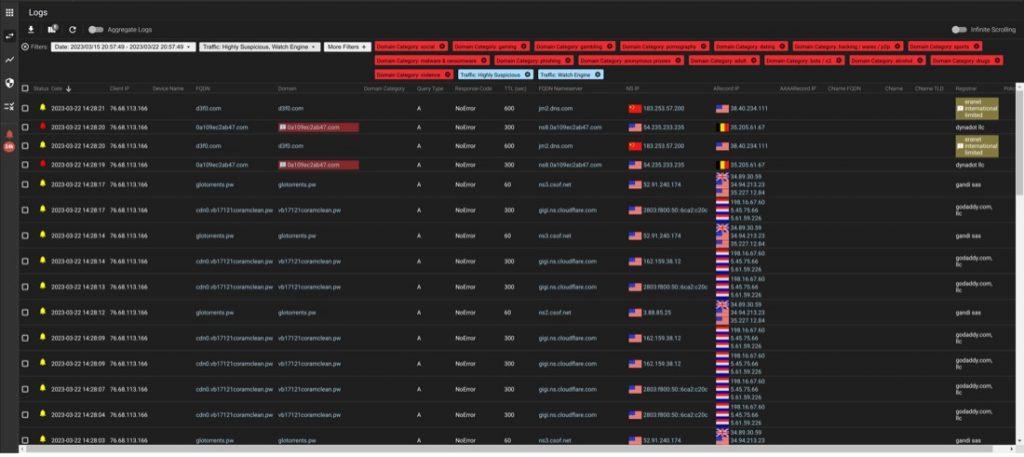
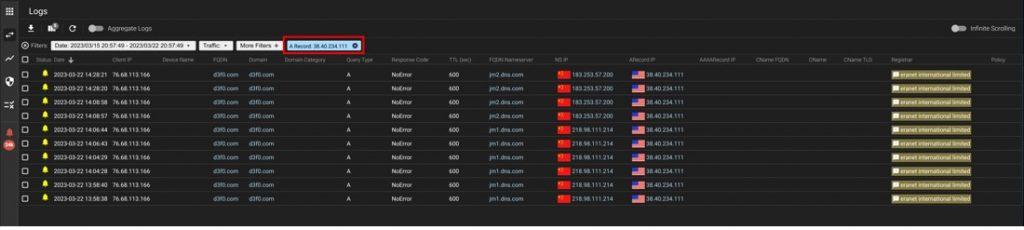
Inside the query logs in the UltraDDR Portal, click on the “X” to remove all of the filters. Then add a single filter for the appropriate Indicator of Compromise: FQDN, domain, or a Record (to filter for an IP Address). You can use this view to find users that have queried for that IOC and that could be infected without anybody knowing it.
Using Categories.
The fourth method is to use categories to help guide you. Categories are an engine that uses feeds of domains outside of the watch engine.
To set up categories, you go into the Policy Engine. Categories show up right away. If they show a green dot, they are set to block domains and hostnames that match that category. Here I have Hacking/Warez/P2P and “Malware and Ransomware” unblocked. However, that will still do the categorization and you can see the results in the logs.
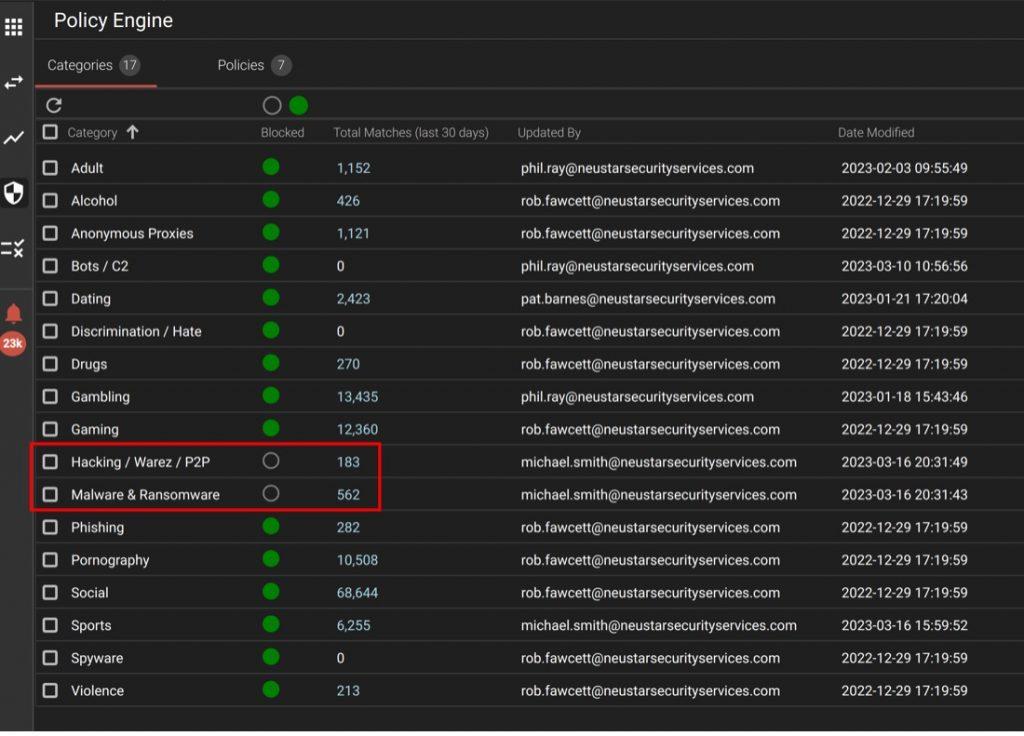
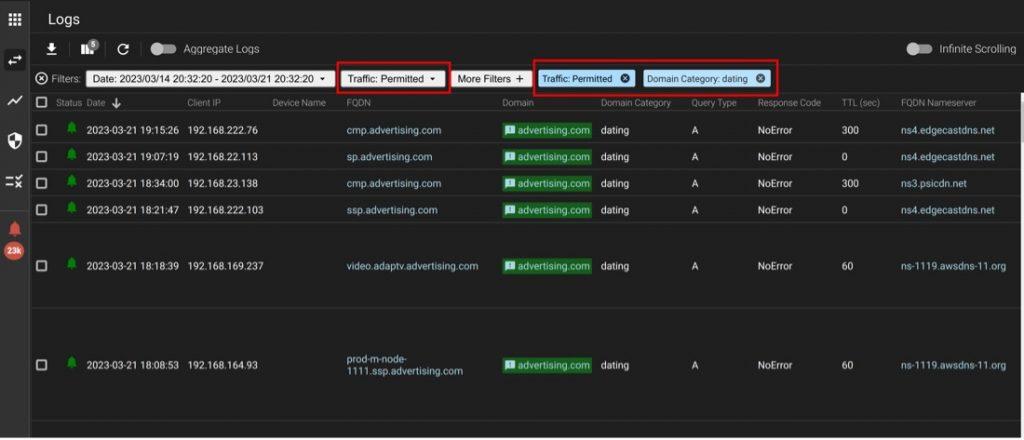
Then inside of the logs view in the portal, you can filter by “Domain Category” and “Traffic: Permitted” to get a view of FQDNs that were categorized but not blocked.
Conclusion.
As they say in the Linux world, “There is More Than One Way to Do It,” or TIMTOWTDI. Hopefully, with this blog post, we’ve shown you several ways to use UltraDDR to hunt for threats and along the way, maybe some neat tricks around filtering query logs. Happy Hunting!

