Whether it was the first denial of service (DoS) in 1974 by 13-year-old David Dennis, the first recognized distributed denial of service (DDoS) in 1996 against NYC ISP Panix or more recent multi-terabit attacks against large cloud providers, DDoS attacks have always been as large or sophisticated as necessary to down or degrade the intended platform, application or entity. When it comes to DDoS, it is often said that there is nothing truly new – old methods are just iterated on or recycled. This is not strictly true, as new application vulnerabilities that enable DDoS attacks are continuously found and used in the latest attacks. However, it often feels true due to recycled attack methods.
Carpet bombing is not a new attack method, but the exploding (pardon the pun) frequency of carpet bomb attacks is a new trend. In the first six months of 2024, 75% of DDoS attacks that Vercara observed leveraged carpet bombing, and now, over half of all DDoS attacks we observe leverage carpet bombing.
Carpet bombing as stealth targeting.
Over the last year or so, size-related DDoS trends represented the highest growth levels at the very top (>100 Gbps) and very bottom (<500 Mbps) tiers of attacks. This also coincides with the dramatic rise of carpet bombing as a percentage of attacks, but why? The largest attacks (>100Gbps and up to multi-terabits per second) are fueled by easy-to-use DDoS tools like dashboards, DDoS-as-a-Service providers, compromised IoT devices forming many Mirai variants, Virtual Private Servers spun up in major cloud services (often for free), and the proliferation of malware leading to more bots as well as larger botnets. The smaller attacks (<500Mbps) are more targeted, with pre-attack reconnaissance being common.
The smaller attacks do not bring down entire platforms or saturate large internet access pipes. They are designed to degrade specific targeted applications or infrastructure while trying to avoid detection. These smaller attacks, as well as some of the larger ones, are also aided by the frequent discovery of new DDoS-enabling application bugs or vulnerabilities. This includes HTTP/2 rapid reset, Infinite Loop, and Continuation Flood. Two major regional conflicts provide motivation and contribute to increased attack frequency. Carpet bombing allows these smaller (and some larger) attacks to be launched amid all this increased noise with the hopes of evading detection and mitigation. But how?
Attempting to evade and overwhelm.
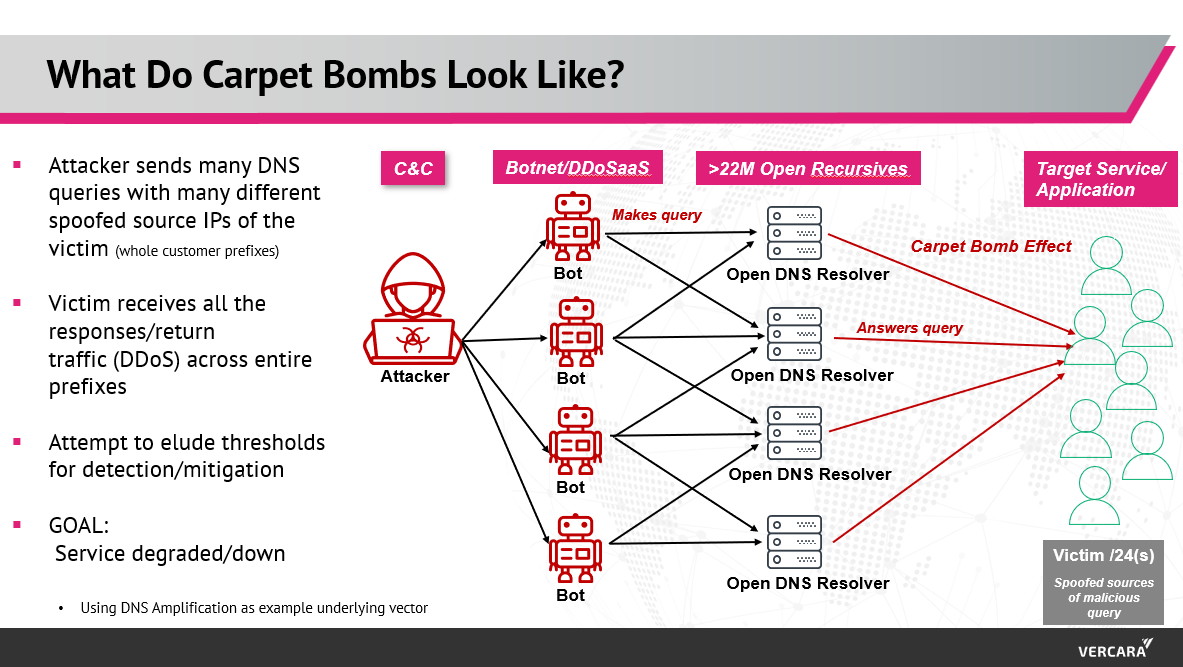
The carpet bomb DDoS method is intended to subvert traditional detection methods and typical mitigation measures. Attackers launch a series of short-duration attacks against many IP addresses in a network block – typically, every IP address in one or multiple /24s (a /24 is 256 contiguous IP addresses). The attackers would first identify the target entity’s IP allocation(s) commonly using a regional internet registry or target the entire prefix (network block) containing the application or system they wish to impact.
By spreading the attack across many target IP addresses, the aim is to evade flow sampling-based detection and blocking of individual attack vectors by falling below per-destination rate-limit-based thresholds used to both detect and invoke mitigations. Using a combination of underlying specific attack vectors per carpet bomb can add to the obfuscation.
Carpet-bombing across multiple BGP prefixes could be an attempt to force the defender to bring multiple networks into mitigation. For some enterprises and service providers architected to redirect traffic and mitigate attacks through security appliances on a per IP address basis, carpet bombs can create load issues. More distributed deployments and system designs handle the impact more elegantly.
How is it done?
Some DDoS attack tools have carpet-bombing options that make it easy to perform these styles of attacks using automation. Frequently, each wave will last less than 3 minutes and may be less than 10 Mbps per destination IP address. Carpet bombing reflects an intelligent attempt to evade detection and mitigation thresholds but uses existing underlying DDoS attack vectors. Attackers frequently use UDP-based reflection vectors including DNS amplification as well as TCP ACK and SYN floods. But, instead of a single or several targets, entire prefixes are targeted with per destination bits per second intended to fall below detection thresholds.
By attacking many different destination IP addresses simultaneously, attackers can also mask their actual target systems or applications – the target could be a single IP on the targeted prefix or several. The aggregate load on the customer access circuit of the many destination IP addresses of the carpet bomb attack could also be intended to impact a non-targeted system that is announced from the same location. Using reflectors (such as open DNS recursive resolvers in a DNS amplification attack) and many different destination IP addresses multiplies the obfuscation options available to the attacker wishing to remain stealthy.
Why the increased frequency?
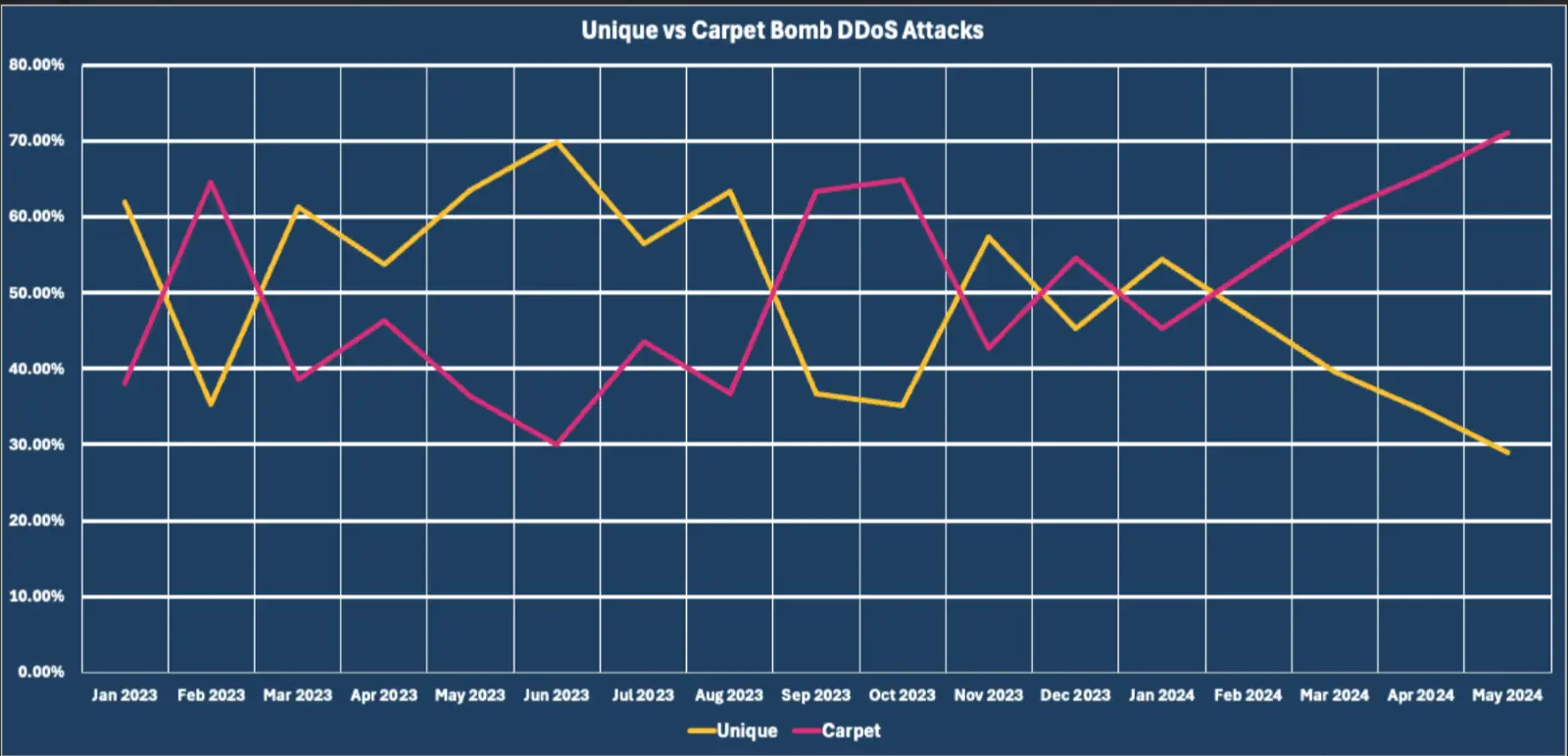
Though the carpet bomb DDoS technique has been around since at least 2016, using various underlying attack vectors (DNS Amplification, SYN flood, etc.), Vercara has noted a dramatic increase in the percentage of attacks leveraging carpet bombing over 2023 and the first half of 2024.
Throughout 2023, carpet bombs (vs. attacking unique single IP addresses) constituted an average of ~49% of all attacks with a number of spikes. In 2024, we have seen some months average over 70% of all DDoS attacks that Vercara observes leveraging carpet bombing – 2024 could aptly be recognized as the Year of the Carpet Bomb. AI and automated attack tools have enabled bursting attacks, shifting attack vectors and attacks such as carpet bombs that attempt to evade detection as well as mitigation.
Increased hacktivist activity fueled by 2 major regional conflicts has also contributed to the increase in carpet bomb usage, with obfuscation potential being a major motivating benefit of carpet bombing.
False positives and alert fatigue.
When an enterprise or Managed Security Services Provider (MSSP) attempts to detect and mitigate carpet bomb DDoS attacks, it can lead to many false positive alerts and notifications. This is due to the lower thresholds required to detect such attacks. Adjusting alert thresholds to catch the lower per IP address attack traffic of carpet bombs can have the unintended collateral impact of also “catching” benign traffic spikes. Now the customer security engineer or SOC analyst must sort through all the alerts to determine which are legitimate and actionable. Elevated levels of false alerts can lead to alert fatigue and ignored alerts.
Systems, appliances, and staff can be saturated by very high numbers of alerts, both legitimate and false. Carpet bombs, by the very nature of their highly distributed attack surface, can produce very elevated levels of alerts by default. Leaving thresholds high could allow carpet bomb DDoS to go undetected. Experienced staff and well-tuned detection are required. How much expertise do engineers have in addressing this threat? What are the related capabilities of the platform that they manage?
Need better tools? We have the technology!
Thanks to the increasing prevalence of carpet bomb attacks, there are even better tools to mitigate them! There are a number of improvements being used to detect with higher efficacy, detect more quickly, and reduce alert fatigue of both staff and hardware. This includes context-based detection that looks at traffic levels targeted at both individual IP addresses and entire prefixes, rolling up individual alerts into aggregated alerts to better manage events, and Machine Learning-curated threat intelligence using known bad sources to detect attack traffic at lower thresholds.
Vercara UltraDDoS Protect and the Vercara Security Operations Center (SOC) have the required scale, experience, expertise, and tools necessary to protect Vercara customers in the Year of the Carpet Bomb.
To learn more about carpet bombing and other DDoS trends, read our biannual DDoS report.

