Bad Actors Have Powerful Tools
Historically, the largest volumetric Distributed Denial-of-Service (DDoS) attacks have used some type of amplification-based attack vector to dramatically increase the size of their attacks. These attacks often leverage flaws or exploits in User Datagram Protocol (UDP) services and vulnerable servers to reflect an attack on its targets using source IP address spoofing. Botnets have now grown so large thanks to IoT and have access to so much bandwidth thanks to extremely well-connected public cloud services; that bad actors (hacktivists, criminal organization or nation-state sponsored) can now launch equally large attacks directly from their own or rented botnets with plentiful attack method options. These powerful DDoS as a Service (DDoSaaS) platforms or botnets for hire no longer require reflectors or amplification to create huge floods of traffic towards their targets to deny service or degrade platforms. Some attack tools now even leverage AI to determine effective attack vectors and shift vectors dynamically for better attack efficacy.
Formerly Rare >1Tbps Attacks Have Become Common
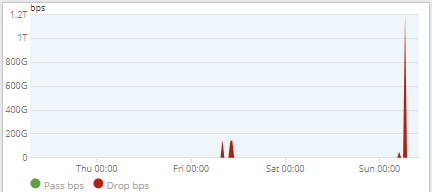
Vercara mitigated such an attack against a hosting and internet services provider last month (October). The attack reached over 1.4Tbps, with Vercara Security Operations Center (SOC) noting they observed a peak of nearly 1.5Tbps and 459Mpps—this is the largest attack in both bits per second (bps) and packets per second (pps) that Vercara has seen to date. Recently, the industry has seen several multiterabit attacks as well, with attack intensity exceeding 500Mpps— the threat is real, and the attackers have massive attack capacity. DDoS attacks exceeding 1Tbps and 400Mpps had been fairly rare but are becoming increasingly common due to the easy availability of attack tools and platforms available to hacktivists and other bad actors.
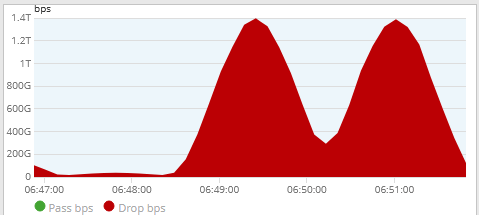

Anatomy of a Small Packet DDoS Attack
A Vercara hosting and internet infrastructure services provider customer had been actively targeted for several days preceding the largest waves of this DDoS attack. Different attack vectors over the course of the campaign created multiple peaks in either bits per second (bps) raw size or packets per second (pps) attack intensity. The highest impact period of the attack was observed in the very early hours of the morning in the United States. Thanks to the best in class technology and automation used in Vercara’s UltraDDoS Protect service, each of the attack waves and shifting attack vectors were automatically detected and mitigated through automation while closely monitored by Vercara SOC. There were several waves peaking over 1.4Tbps and attack intensity reaching 459Mpps.
The attack shifted from a DNS flood targeting UDP port 53 (DNS) to TCP SYN and ACK floods targeting port 80 (http). SYN and ACK floods are designed to tie up resources (memory, CPU, etc.) of targeted systems as well as congesting infrastructure in the path of the attack which can create bottlenecks in network architecture. The vast majority of attack packets were <150 bytes which necessitated a very large attacking botnet with >225,000 total source IP addresses observed. The attack sources were very broadly distributed geographically. The SYN and ACK flood vectors were sourced from high number ephemeral ports (vs. port 80 or 443). Vercara mitigated the attack upstream from the customer’s direct internet access providers, sot the performance and availability of the targeted customer platform were not impacted even as attack methods shifted and attack sizes reached unprecedented levels.
Takeaways
The SOC-tuned detection and countermeasures were very effective in automatically detecting and mitigating this attack despite the combination of very small packets and a large number of source IP addresses involved in the peak SYN and ACK flood being unprecedented. This attack graphically illustrates the current capabilities of attackers to execute exceptionally large direct path DDoS without reflection or amplification necessary. The attackers have tools at their disposal, with the required number of bots, to leverage high packet-per-second rate attacks utilizing very small packets. Small packets can be extremely hard for infrastructure to process at high packet rates, which leads to resource saturation and unavailability. DDoS stressor platforms (DDoSaaS) have the ability to launch very large and very sophisticated attacks that can be manually and potentially automatically tailored to the intended target(s).
Do You Have a Plan?
Why is this incident important? This record-setting attack highlights preparedness. There are some best practices for enterprises to follow.
- Keep up with the current DDoS threat environment/trends, especially those that target the industry that you are in.
- Keep an updated runbook for DDoS attack defense.
- Run DDoS drills periodically to test internal and external processes/capabilities.
- Ensure your DDoS mitigation provider has adequate capacity/capability to mitigate multi-terabit and >500Mpps DNS or SYN/ACK floods.
Get Prepared With UltraDDoS Protect
UltraDDoS Protect’s global, high-capacity platform leverages Machine Learning-assisted Threat Intelligence to provide flexible and automated DDoS mitigation. UltraDDoS Protect is managed by Vercara’s 24x7x365 SOC team made up of DDoS experts that have years of experience mitigating thousands of attacks each. They continuously monitor for new attacks and manage mitigation configurations when tuning is required. They are also available to work with you on proactive tuning and adjustments between attacks. The SOC is an extension of the customer’s security team. Vercara UltraDDoS Protect has >15Tbps of DDoS mitigation capacity spread across 16 global DDoS and Application Security nodes. UltraDDoS Protect has the capacity to mitigate attack speeds/intensity in the 10s of Bpps. UltraDDoS Protect has the cability to mitigate multiple multi-terabit attacks simultaneously. Automation is a key design objective for the UltraDDoS platform to enable faster speed of response, predictability, and scale of operations. Digital Trust, in this case, is enabled by Vercara’s ability to preserve the uptime and performance of customer applications or platforms.
To find out more about Vercara DDOS solutions, explore here. Learn more about current DDoS trends and Vercara DDoS stats here.
[BR1]UltraDDoS product page
[BR2]1st 6 months of 2024 DDoS webinar

