In the world of cyber security, data is an incredibly powerful tool. The right data can help you detect attacks, discover vulnerabilities, and, more importantly, recognize new and emerging techniques used by cyber criminals.
Vercara’s Security Operations Center knows just how valuable data can be in defending against cyber-attacks. To help you develop a better understanding of emerging DDoS attack techniques and better defend your organization, our SOC team has compiled the 2023 attack data from our platform, UltraDDoS Protect, and identified emerging trends.
2023 DDoS trends
In 2023, Vercara observed and mitigated over 65,000 DDoS attacks, with February being the busiest month with 8,977 attacks. During the summer months, there was a decline in activity, which we attribute to malicious actors conducting more targeted, deliberate, and purposeful attacks instead of conducting spraying attacks and hoping to have some sort of effect.
Several factors are to cause for the increasing DDoS landscape:
- Geo/political conflicts: Regional conflicts have fueled the rise of hacktivists that have targeted a wide range of industries as well as countries. Hacktivists conduct DDoS attacks against countries or companies they feel are providing support to or aiding their side’s adversaries.
- Easy-to-use DDoS tools: The proliferation of DDoS tools and scripts that are hosted on code repository sites like GitHub, such as “Build Your Own Botnet”, allows any individual the capability to conduct or participate in DDoS attacks.
- DDoS-as-a-Service: There has been an increase in groups advertising services to conduct DDoS attacks on behalf of someone for a small amount of money. By using these “service providers,” individuals don’t have to invest in building out their own infrastructure and can use an already established infrastructure.
- Compromised Internet of Things (IoT) devices: The explosion of Internet-connected IoT devices dramatically increased the DDoS attacks. The majority of IoT devices are built for cost, ease of use, and planned obsolescence. Security measures are usually considered last, if at all. Because IoT devices have weak security measures, they are easily compromised, and malware is installed to build out botnets that are used for DDoS attacks.
- Virtual Private Servers (VPS): Malicious actors look at compromising VPS infrastructure because they offer substantially larger internet connections than residential broadband subscribers or mobile devices. This allows the attackers to conduct more powerful DDoS attacks.

DDoS mega attacks in 2023
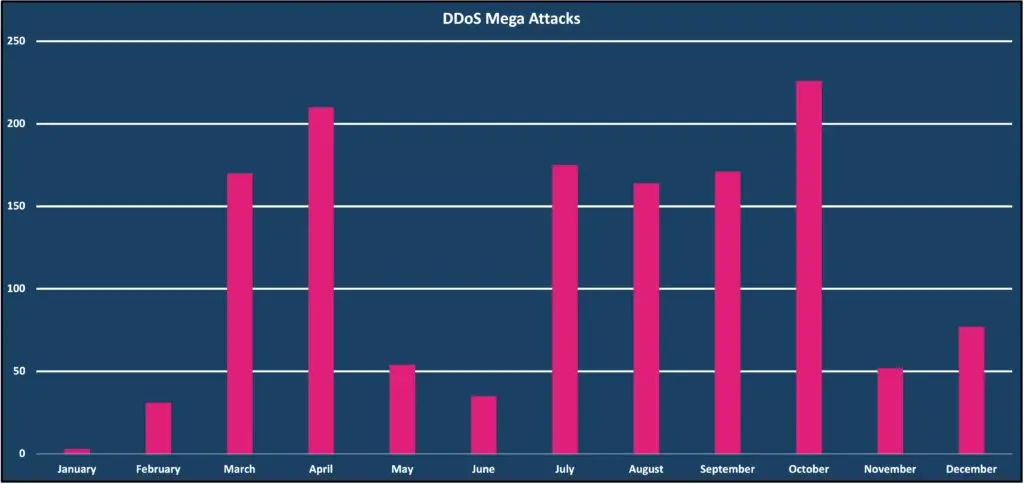
Vercara classifies mega DDoS attacks as attacks consisting of 100 Gigabits or more. In 2023, Vercara observed and mitigated 1,368 mega DDoS attacks with no degradation to legitimate internet traffic towards the targeted sites. Compromised VPS infrastructure is leading to an increase in mega attacks that offer significant bandwidth to conduct attacks. Mitigating these mega attacks takes a purposefully built third-party DDoS mitigation solution with adequate capacity to absorb the volume that these attacks bring.
Hacktivists armed with powerful stressor tools backed by large botnets and easy access to plentiful bandwidth leveraging free VPS solutions will likely continue this trend into 2024.
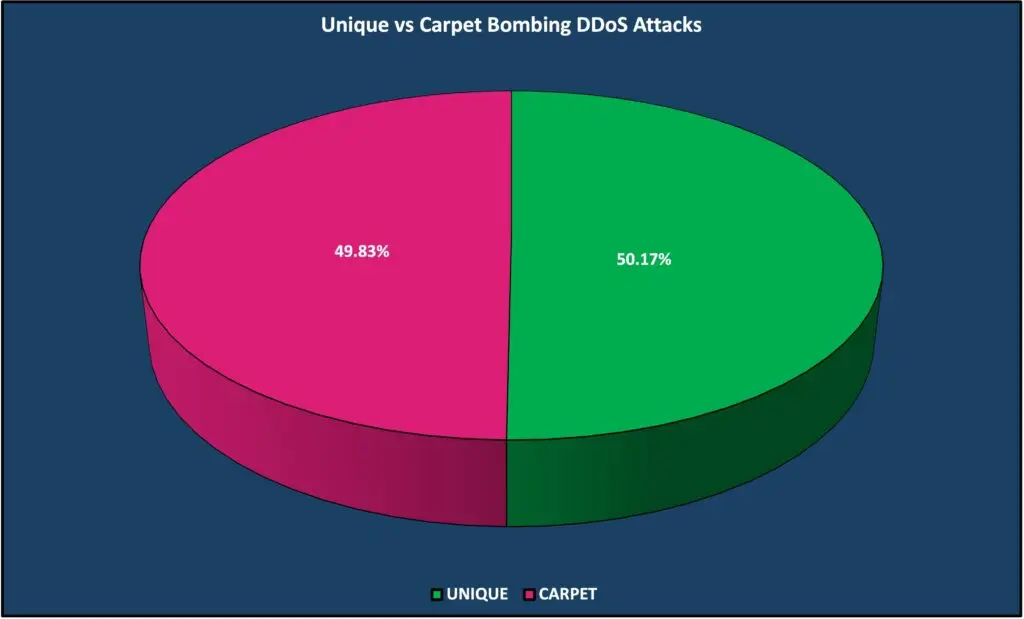
2023 Carpet Bombing DDoS attacks
During 2023, Carpet Bombing DDoS attacks accounted for almost 50% of all observed DDoS attacks and saw a 52% increase from January to December 2023. Carpet Bombing attacks attempt to rotate targeted destinations within the same ASN or network block to avoid alert and mitigation thresholds or to overload mitigation gear by ramping large amounts of networks and endpoints.
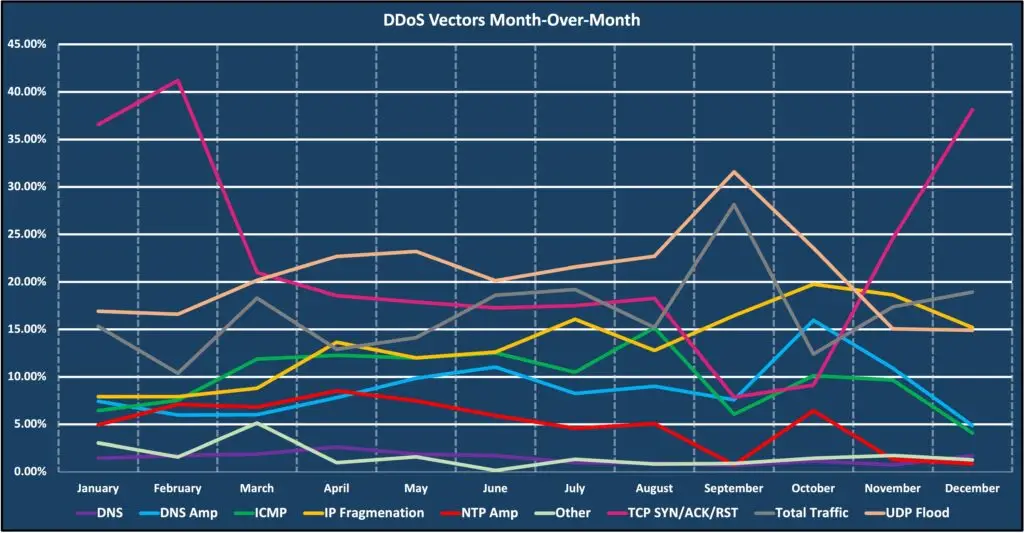
2023 top DDoS attack vectors
For 2023, User Datagram Protocol (UDP) was the most prominent DDoS attack vector observed. Protocol attacks over UDP are commonly used because they don’t use a two-way handshake like TCP, making it easier to do source routing or “spoofing” the source of the traffic. The second most prevalent DDoS vector was Total Traffic, which typically correlates to Carpet Bombing style attacks. The TCP-ACK vector was third and abuses the TCP three-way handshake, consuming endpoint resources by keeping connections established while waiting for the completion of the three-way handshake.

Just looking at the end-year numbers does not provide a true understanding of how malicious actors have adjusted which DDoS vectors they were using. Throughout 2023, attacks utilizing the TCP three-way handshake saw a continuous decline throughout the year but rose sharply in the last two months of the year. UDP and Total Traffic saw a month-over-month increase throughout 2023. DDoS attacks, both against DNS servers and using DNS amplification, saw a comeback in 2023 and gradually increased throughout the year. DNS reflection or amplification attacks leverage the ~20M open recursive DNS resolvers across the internet.
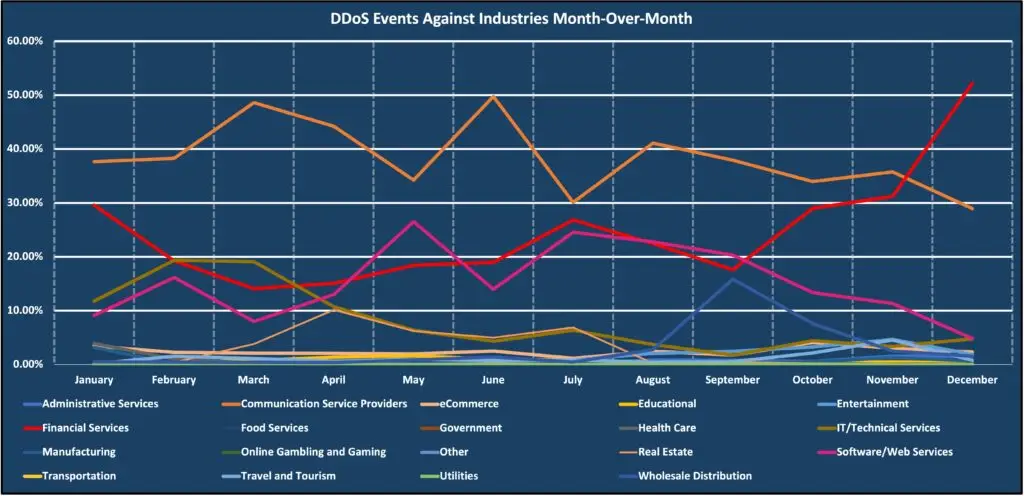
2023 DDoS attacks by industry
The Communication Service Providers industry was the number one target for DDoS attacks in 2023. This industry represents resellers and SaaS providers that provide hosting and other services to many different industries. The Financial Services industry was second and, throughout 2023, was in the top three every month. The Software/Web Services industry was the third most targeted industry in 2023 and was also in the top three every month.
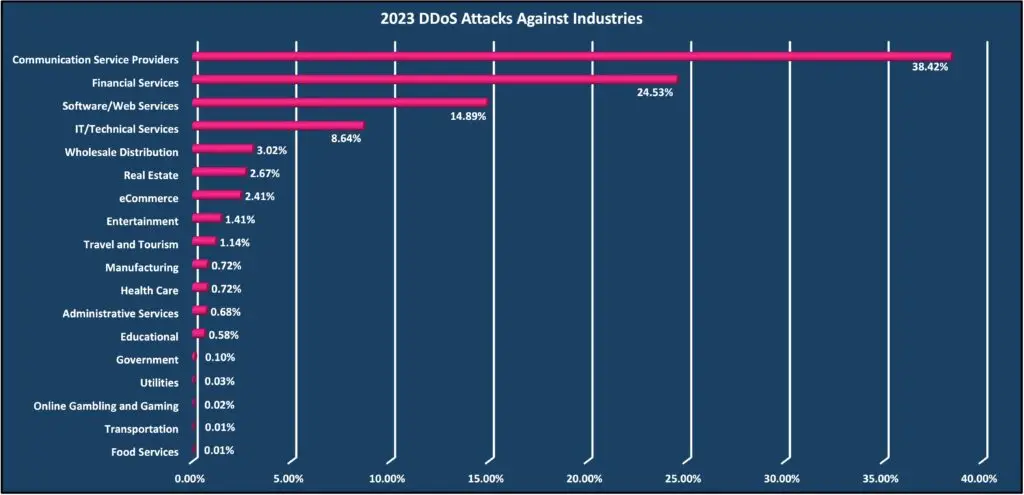
Looking at the month-to-month trends, the Financial Services industry saw a steady increase and, in December, became the number one targeted industry, displacing the Communication Service Providers industry for the first time in 2023.
2024 DDoS trends to watch out for
As the new year begins, there are a range of DDoS attack trends you should keep an eye on to better protect your organization, including:
- Attacks motivated by conflict: Regional conflicts will continue to inflame nationalistic & ideological tensions to motivate DDoS campaigns.
- State-sponsored hackers: Nation-states will continue to fund and provide loose guidance to hacktivists, criminal groups, and patriotic hackers to add a layer of plausible deniability.
- Targeted attacks: More high-impact cloud services, financial institutions, and gov’t sites will be targeted.
- AI-assisted DDoS attacks: These attacks will be automated, quickly morphing, flexible, and have higher efficacy.
- Application-targeting request floods: Attacks smaller than 50Mbps will be highly effective, especially when guided by the discovery of new vulnerabilities.
- Ransom-DDoS and ransomware: These techniques will be a powerful combo leveraged by criminal groups and potential hacktivists.
With these new and emerging threats taking center stage, there’s no better time to upgrade your DDoS protection. To learn how our UltraDDoS Protect solution can enhance your cyber security, visit our product page.

