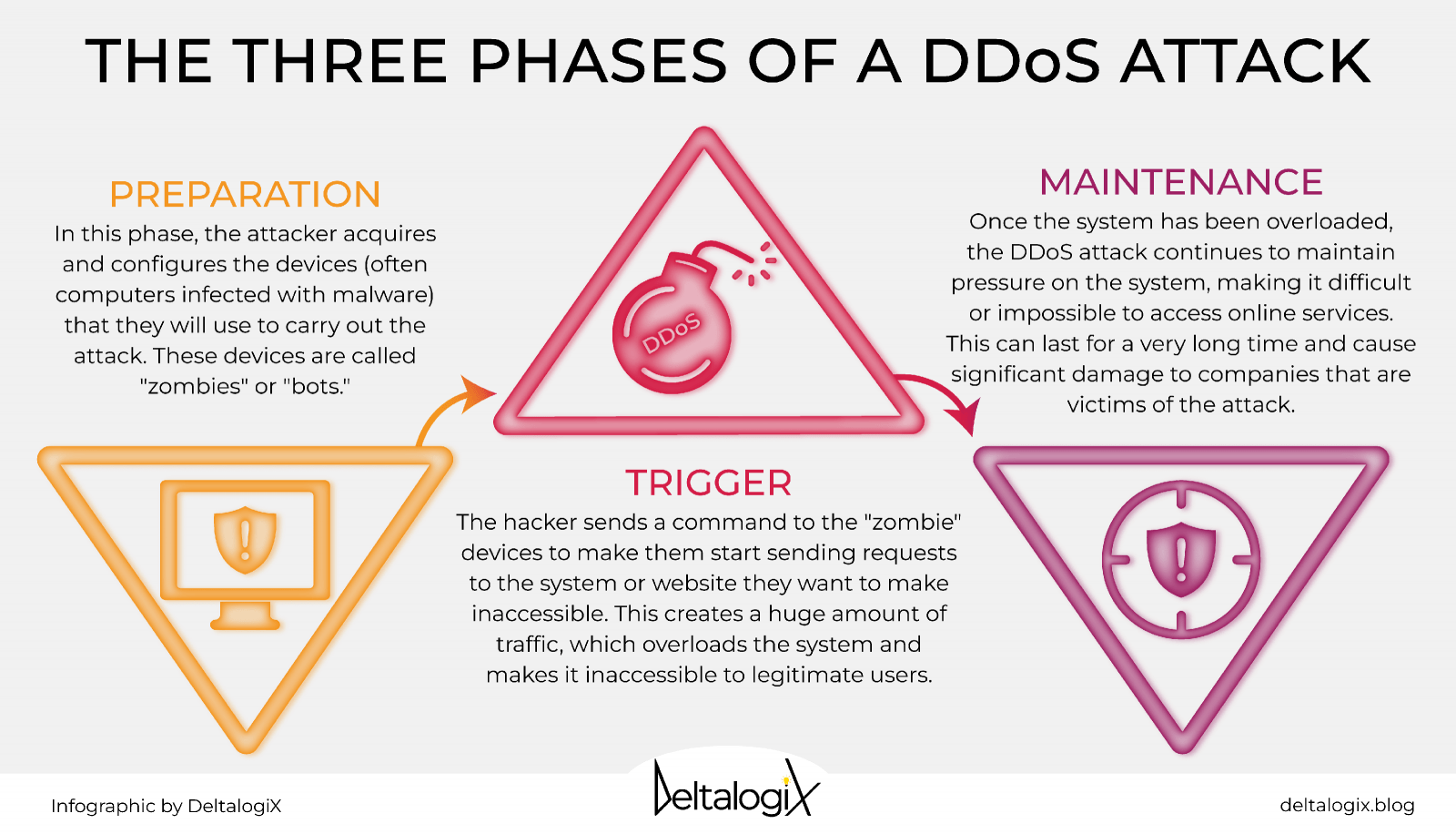
Does your enterprise need DDoS Mitigation? The answer is yes
It shouldn’t surprise anyone in business that attacks on cybersecurity are on the rise. Just in the first quarter of 2022, 92% of data breaches were brought on by cyber attacks, and the number of DDoS attacks are supposed to skyrocket to 15.4 million across the globe in 2023 alone. This is where DDoS mitigation can help.
The purpose of DDoS mitigation is to successfully protect a network or server from a Distributed Denial of Service (DDoS) attack. A quality DDoS mitigation service guards potentially vulnerable systems with advanced tools and strategies to protect against these attacks and secure your digital assets while keeping them accessible.
Types of DDoS attacks
To truly understand the necessity of a DDoS mitigation solution, it’s important to familiarize yourself with the types of DDoS attacks. Each type has its own unique approach, but all share the same objective—to incapacitate your network, service, or server. Here are three examples of different DDoS attacks.
Volume-based attacks
The digital equivalent of overwhelming a crowd with sheer numbers, volume-based attacks aim to congest a network’s bandwidth, halting normal operations. These attacks are measured in bits per second (bps) or packets per seconds (pps).
The largest volumetric attack recorded in 2020 came in at an astounding 2.3 Tbps. Attacks of this size are becoming more common. A potent DDoS mitigation solution should be able to handle such volumes and maintain your enterprise’s accessibility, even under heavy bombardment.
Protocol attacks
Protocol attacks, on the other hand, target network resources rather than bandwidth. These attacks exploit server processes, firewalls, and load balancers, limiting the number of sessions one device can handle.
They focus on specific parts of your infrastructure, making them a more targeted form of attack. Considering that we saw an attack intensity record of 809 million packets per second in 2020, a robust DDoS mitigation solution should offer strategic solutions to these attacks and ensure your infrastructure remains unscathed.
Application layer attacks
Lastly, we have application layer attacks. These attacks mimic normal user behavior and target the weakest link in any network’s security — the application layer.
These kinds of attacks are often harder to detect as they operate on a level that doesn’t immediately overwhelm bandwidth or server resources, but rather slowly chips away at your system.
When a DDoS attack hits, it can take down your enterprise’s website or network, causing severe disruption to operations. A short period of downtime can have significant consequences on everything from workflow to brand reputation to financial impacts.
A DDoS attack can even lead to the loss of crucial data. It’s not just about the immediate aftermath – the long-term effects can ripple through your business for months or even years.
The impact of DDoS attacks on businesses
Direct and indirect costs of DDoS atttacks
Material and immaterial costs of DDoS attacks against unprotected systems go beyond the immediate scope of consideration. But even thinking in terms of direct costs, like impact to your finances, you’re looking at an average cost of 40,000 per hour, DDoS attack—and that isn’t including costs associated with ransomware.
Downtime and the cost of getting your systems back online are also nothing to overlook. These costs can quickly escalate, particularly for businesses that rely heavily on their online presence.
Indirect costs, though more difficult to quantify, can be even more significant. Immaterial costs can have more far-reaching consequences, and some of these costs include:
- Loss of customer trust
- Decreased future sales
- Potential legal action taken against your business if sensitive data is compromised
When customers choose your business, they’re placing their trust in your ability to deliver a product or service – and to protect their data. A DDoS attack can shatter that trust in an instant.
Moreover, the damage to your reputation can be extensive and long-lasting. Today’s customers are savvy – they pay attention to how businesses handle security incidents, and they make decisions based on what they see. In the wake of a DDoS attack, you may find yourself struggling to win back the trust of your customers and restore your tarnished reputation.
A Real-world example of a DDoS attack
In the first half of 2020, Vercara mitigated a 1.17 Tbps Connectionless Lightweight Directory Access Protocol (CLDAP) attack — comparable to some of the largest attacks on record.
What do CLDAP attacks do? Imagine a CLDAP Reflection Attack as a nasty form of business sabotage. It’s like a rival company sending a flood of customers to your store, pretending you invited these customers.
They do this by misusing a faster and more efficient way of communicating information (called CLDAP).
The rival sends a request to this delivery service, but they trick the service into believing the request came from your company. As a result, the delivery service, thinking it’s responding to your request, sends a huge number of customers to your store. Your store, unable to handle the sudden influx of customers, gets overwhelmed.
Just as one example of a DDoS attack, CLDAP attacks can absolutely disrupt your business workflow.
A deep dive into DDoS mitigation
DDoS mitigation is designed to identify, counteract, and learn from DDoS attacks. Here’s a closer look at what each step entails:
Detection
Detection is the powerful first step in DDoS mitigation. A change in traffic flow can be an imminent signal that an attack is incoming. An effective DDoS mitigation service will have advanced detection capabilities that can differentiate normal spikes in traffic from malicious ones.
Diversion
Once a potential DDoS attack is detected, the next step is diversion. This involves rerouting the incoming traffic away from your network to protect your resources. This can be achieved via DNS (Domain Name System), which is an always-on solution, or via BGP (Border Gateway Protocol), which can be always-on or activated on-demand.
Filtering
The diverted traffic is then subjected to filtering—the legitimate traffic from the malicious. Sophisticated DDoS mitigation services employ advanced algorithms and techniques to identify patterns associated with DDoS attacks, ensuring that only clean traffic reaches your network.
Analysis
After successfully thwarting a DDoS attack, it’s important to gather as much information as possible about the incident to prevent future attacks.
The benefits of DDoS protection and mitigation
The complexity of DDoS attacks for an enterprise can feel overwhelming, but working with a trusted mitigation partner can reduce the stress. Plus, the risk of being the target of a DDoS attack is not a matter of “if” but “when.”
As the number, intensity, and complexity of these attacks continue to grow, the question is not whether you need DDoS mitigation, but how urgently you need it.
Maintaining business continuity
DDoS attacks can significantly disrupt your operations, causing outages and downtimes that not only impact your bottom line but also frustrate your customers. With DDoS mitigation, you ensure the availability and uptime of your services, reducing the risk of operational downtime, and consequently minimizing lost revenue due to service disruptions.
Safeguarding reputation and customer trust
Any disruption can lead to customer dissatisfaction, tarnishing your brand’s image and reputation. DDoS mitigation service providers ensure a seamless user experience by maintaining robust security measures that protect your business’s reputation and foster customer trust.
Protecting your data network infrastructure
DDoS attacks can be a precursor to more sinister threats, such as data breaches. By ensuring the integrity of your network infrastructure, you prevent potential simultaneous attacks that may exploit a compromised network. DDoS mitigation companies play a crucial role in this.
Cost savings
The financial implications of a successful DDoS attack can be severe. These include costs associated with downtime, data breaches, and long-term reputational damage. By investing in , you can minimize these potential costs.
Compliance with regulations
Cybersecurity regulations mandate businesses to have robust security measures in place. DDoS mitigation helps fulfill these requirements, reducing legal and regulatory risks and demonstrating due diligence to regulators and customers.
Remember, the cost of investing in DDoS protection is nothing compared to the potential damage that a successful DDoS attack could cause.
DDoS mitigation services
Today’s DDoS mitigation solutions are not just about redirecting traffic; they also need to intelligently analyze incoming traffic, distinguishing between legitimate users and malicious bots.
The best DDoS mitigation services offer an always-on, cloud-based solution or a blend of cloud-based protections and on-premise DDoS mitigation appliances (including hybrid options), ensuring a comprehensive defense against both volumetric and application-layer attacks.
Learn more about DDoS mitigation technologies with these blogs:
- DDoS Mitigation Technologies Part 1: Overview
- DDoS Mitigation Technologies Part 2: ISP Scrubbing Centers
- Emerging Security Threats to Watch in 2023, Part 3: The Next Major DDoS Campaign
- DDoS Mitigation Technologies Part 4: Remotely Triggered Black Hole
- DDoS Mitigation Technologies Part 5: Create Your Plan
Delivery options
Cloud-based
The ability to adapt and respond to threats quickly and efficiently is paramount. For businesses seeking flexibility, scalability, and ease of management, cloud-based DDoS mitigation is a prime solution that ticks all the right boxes.
In the cloud, 24/7 cybersecurity protection for your online assets, no matter where they reside. Your online services are protected from being overwhelmed by traffic from multiple sources, effectively preventing the service from functioning as intended.
Cloud DDoS mitigation services, like Vercara’s UltraDDoS Protect, work by spreading the incoming traffic across a network of servers. These servers are located in various data centers around the world, which is part of what makes cloud-based mitigation so effective. By distributing the traffic, the attack is diluted, and its impact is lessened.
On-premise
But maybe you like to keep things close to home. That’s where on-premises solutions step in. This is for the businesses that are steadfast, that want the keys to the castle and the control that comes with it.
On-premises means integrating Vercara’s advanced security technology directly into your network. It’s about responding to threats with a snap of your fingers. It’s about having the same advanced features found in UltraDDoS Protect, but in your own backyard. And with Vercara’s round-the-clock customer support, you’ve always got an expert in your corner, ready to spar with any emerging threats.
Hybrid
Hybrid solutions offer the blend of the cloud’s scalability with the security of on-premises deployments. It’s the best of both worlds, tailor-made to tackle the relentless landscape of cybersecurity threats.
This approach provides an optimal balance between immediate on-site detection and the high-capacity defenses of the cloud, offering comprehensive protection against both volumetric and application layer DDoS attacks.
Scalability
The scalability of your DDoS mitigation service is vital as DDoS attacks have grown larger and more complex over the years. A service that can adapt and scale with the intensity of the attacks ensures you won’t be vulnerable when an unexpectedly large attack comes your way.
Flexibility
Just as with scalability, flexibility is a crucial feature of your DDoS mitigation strategy. As we’ve seen, attacks are not static; they evolve over time. Your DDoS mitigation needs to be as agile as the threats you’re facing. A flexible service will respond effectively to a range of attack types and sizes, minimizing the potential impact on your business.
Reliability
When an attack occurs, you need a service that will step up and protect your enterprise without fail. The best DDoS mitigation services have proven track records and solid reputations. They offer 24/7 support and guarantee minimal downtime, even in the face of the most severe attacks.
Network capacity and size
The capacity of your DDoS mitigation service’s network is a vital consideration. The larger the available bandwidth, the more traffic it can manage. A large network spread across multiple locations also provides resilience against localized attacks.
Also, consider the deployment model of your DDoS mitigation service. Cloud-based options are just as secure and require no on-premise equipment. Hybrid models, which combine on-premise appliances with cloud DDoS mitigation, are another option.
Processing capacity
The processing capacity of your DDoS mitigation service can be a deciding factor in its effectiveness. High forwarding rates ensure that legitimate traffic can pass through while malicious traffic is blocked.
Low latency
Latency is the delay between a user’s action and the system’s response. The best DDoS mitigation strategies aim to keep latency low, ensuring that users can continue to access your services even during an attack.
Time to mitigation
The time to mitigation is the period between the arrival of malicious packets and the commencement of scrubbing by your mitigation provider. The faster this happens, the less impact the attack has on your operations. Top-tier DDoS mitigation providers pride themselves on their rapid response times, often measured in seconds rather than minutes.
Network layer mitigation
Null routing – remotely triggered black hole
Remotely triggered black holes (RTBH) are a commonly used DDoS mitigation technique that is utilized when the costs of defending against an attack outweigh the benefits or when the attack is so large it impacts other organizations.
This technique works by diverting all traffic, both legitimate and malicious, to a non-routable address space using Border Gateway Protocol (BGP).
The key advantages of RTBH include its unlimited capacity, lack of need for advance preparation, and the ability to combine it with BGP communities to selectively route traffic based on distance. However, it requires an enterprise to own and manage the routing for a network block or Autonomous System Number (ASN).
A significant drawback is that it indiscriminately drops all traffic, rendering the website and other services inaccessible, thereby effectively mimicking the impact of a successful DDoS attack.
At the network layer, DDoS attacks can be particularly harmful. They aim to overwhelm your network’s infrastructure, leading to service outages. There are several mitigation techniques available.
Sinkholing
Sinkholing is another effective mitigation technique. Like its real-world counterpart, a digital sinkhole ‘swallows’ incoming traffic. Traffic that lands in the sinkhole is analyzed and blocked, ensuring that unwanted packets do not reach their goal. This method not only helps to mitigate DDoS attacks but also provides valuable insight into attack patterns and sources.
ISP scrubbing center
Internet Service Provider (ISP) scrubbing centers are facilities designed to protect network infrastructure from DDoS attacks. These attacks attempt to overwhelm a network with traffic, causing a slowdown or complete outage of services.
Here’s how it works: When a DDoS attack is detected, the targeted traffic is rerouted to a scrubbing center. The term “scrubbing” refers to the process of separating malicious traffic from legitimate traffic.
Using advanced algorithms and detection methods, the scrubbing center identifies and filters out the harmful data packets associated with the DDoS attack. The legitimate traffic is then forwarded on to its intended destination, ensuring that normal service continues with minimal disruption.
Cloud-based scrubbing center
Cloud-based scrubbing centers are a specialized infrastructure designed to mitigate DDoS attacks by “scrubbing” malicious traffic away from legitimate traffic. These centers are part of a cloud-based service, meaning they leverage the distributed nature and scalability of the cloud to handle large-scale DDoS attacks.
Stopping IP masking
IP masking is a common tactic used by attackers to disguise the source of a DDoS attack. This can be stopped with packet filtering, a process that scrutinizes packets and discards those from suspicious or unknown sources. It’s a powerful tool in the fight against DDoS attacks, adding an extra layer of security to your defenses.
Application layer mitigation
DDoS attacks are not just a threat to your network layer; they can also target your application layer. This is where your applications interact with user data and where a successful attack can lead to serious data breaches.
Mitigating DDoS attacks at the application layer requires sophisticated DDoS mitigation software that can employ multiple inspection methods to identify legitimate traffic. This helps ensure your applications continue to function optimally during an attack, providing a seamless experience for your users.
Secondary asset protection is another crucial aspect of application layer mitigation. It’s not just your primary assets – your websites and online services – that need protection. Any component of your digital infrastructure can be a target, and a successful attack on a secondary asset can have ripple effects across your enterprise.
DNS name server protection
DNS name servers are a vital part of your online presence, and an attack on your DNS servers can make your websites and services unreachable.
Protection for your DNS name servers is a key part of mitigating DDoS attacks. This involves filtering unwanted traffic and blacklisting malicious URLs, helping to maintain the availability and integrity of your DNS records.
Application protection
DDoS attacks can target vulnerabilities in your applications. Whether it’s a web application firewall (WAF) bypass or an exploit of a specific software vulnerability, these attacks can cause significant disruption and potential data loss.
This involves keeping your applications updated to patch any known vulnerabilities, and using DDoS mitigation software that can identify and block attack vectors targeted at your applications.
DDoS mitigation techniques
When it comes to mitigating DDoS attacks, it’s important to have a diverse arsenal of protection techniques at your disposal. This includes everything from basic IP blacklisting to more complex methods such as rate limiting and anomaly detection.
Planning for scale
Scalability is a key factor when choosing a DDoS mitigation solution. Look for solutions that can handle large-scale attacks without affecting the performance of your network or applications.
Reducing attack surface area
Reducing your attack surface area is all about limiting the number of ways an attacker can target your enterprise. This can involve everything from securing internet connections to minimizing the amount of exposed data.
A key aspect of this is differentiating between normal and abnormal traffic. Ensure you are using a DDoS mitigation solution that allows you to quickly identify and respond to any suspicious activity.
Firewalls for sophisticated application attacks
Firewalls can protect against a range of threats, from simple volumetric attacks to more sophisticated application layer attacks, but not all firewalls are created equal.
When it comes to mitigating DDoS attacks, you need a firewall that can handle complex threat patterns and adapt to evolving attack strategies.
Mitigation countermeasures
Countermeasures are an essential part of any DDoS mitigation strategy. This can include TCP authentication, which verifies the legitimacy of TCP connections, and HTTP authentication, which protects your web applications from unauthorized access.
But countermeasures aren’t just about blocking attacks. They also involve detection of misuses, identifying when and how your systems are being exploited. This enables you to respond quickly to threats and minimize the impact of any successful attacks.
How to choose the right DDoS mitigation provider
Here are some key factors to consider:
- Experience and expertise: Aim to work with a mitigation provider who has a proven track record in mitigating DDoS attacks. They should have a deep understanding of the evolving threat landscape and be able to provide you with tailored solutions.
- Comprehensive protection: A good DDoS mitigation provider should offer comprehensive protection that covers all types of DDoS attacks, from volumetric attacks to sophisticated application-layer attacks.
- 24/7 monitoring and support: DDoS attacks can happen at any time, so you need a provider that offers round-the-clock monitoring and support. They should be able to respond quickly to attacks and minimize downtime.
Scalability
As DDoS attacks grow in size and frequency, it’s essential to have a DDoS mitigation solution that can scale with your enterprise. The best DDoS mitigation providers have the infrastructure and resources to handle even the largest attacks without disrupting your operations.
Flexibility
Your DDoS mitigation provider should be able to adapt to the changing threat landscape and provide you with the most up-to-date protection.
Moreover, they should offer flexible deployment models. Whether you prefer an on-premise DDoS mitigation solution, a cloud-based service, or a hybrid approach, your provider should be able to accommodate your workflow requirements.
Reliability
Your mitigation provider should have a robust infrastructure that can withstand even the largest attacks. In addition, they should have a proven track record of mitigating attacks quickly and effectively.
Reliability also extends to customer service. Your provider should be responsive and helpful, providing you with timely updates and support during an attack.
Pricing and SLAs
What to look for in pricing features
When it comes to DDoS mitigation services, pricing models and service level agreements (SLAs) can vary widely. It’s essential to understand the different pricing models to choose the right one for your enterprise.
- Pay as you go
This model is highly flexible, as you only pay for the service when you use it. However, the costs can quickly add up if you experience a sudden surge in attacks.
- Pay as you go based on attack volume
Some providers charge based on the volume of traffic during a DDoS attack. While this can be cost-effective for smaller attacks, large-scale attacks can lead to higher costs.
- Service-based pricing
With service-based pricing, you pay a fee for a specific set of services, such as monitoring, detection, and mitigation. This model allows you to know exactly what you’re paying for and can be cost-effective if you require comprehensive protection.
- Flat monthly fee
Some providers charge a flat monthly fee for their DDoS attack mitigation This model provides predictable costs and is often bundled with other services, making it a good choice for enterprises that require comprehensive, ongoing protection.
In addition to the base pricing model, some providers offer additional features at an extra cost. These can include advanced analytics, custom reporting, and premium support services.
- Uptime guarantee: This guarantee assures that their services will be available a certain percentage of the time, typically 99.9% or more.
- Protection levels: Different providers offer varying levels of protection, from basic volumetric attack mitigation to sophisticated application-layer attack protection.
- Support service levels: Support is a critical factor in DDoS mitigation. When an attack occurs, you need fast, reliable support to minimize downtime and damage. Look for providers that offer 24/7 support and quick response times.
DDoS mitigation across industries
To truly understand the necessity of a DDoS mitigation solution, it’s important to familiarize yourself with the types of DDoS attacks. Each type has its own unique approach, but all share the same objective—to incapacitate your network, service, or server. Here are three examples of different DDoS attacks.
eCommerce
A single minute of downtime can lead to significant revenue loss, and a DDoS attack can cause hours, if not days, of downtime. The success of an eCommerce business is directly tied to its website’s uptime. A website that’s frequently down, slow to load, or experiencing other performance issues can quickly lose customers to competitors.
DDoS attacks can significantly degrade the performance of your business’s website or even take it offline, leading to a poor customer experience and lost sales.
Mitigating DDoS attacks is crucial for eCommerce businesses to maintain site availability and uptime, protect customer data and trust, and ensure a smooth customer experience and purchase journey.
Finance
Financial institutions handle sensitive data and provide essential services, making them prime targets for DDoS attacks. In 2023, notorious hacktivist group Killnet announced it would be targeting the Western banking system, targeting European banks s SWIFT, IBAN, and other money transfer systems—marking the scale at which these kinds of attacks can occur.
Cybersecurity in the financial sector isn’t just about protecting assets; it’s about ensuring the continuity of services that people depend on every day. A successful DDoS attack could disrupt these services, causing considerable inconvenience and potential financial loss for customers.
A DDoS attack on a financial institution can disrupt operations, prevent customers from accessing their accounts, and damage the institution’s reputation. The resulting loss of trust can lead to customers moving their business elsewhere.
DDoS mitigation for finance is about more than just keeping services online. It’s about ensuring continuous access to financial services, protecting sensitive financial data, and complying with industry regulations and standards.
Healthcare
With advancements in technology, healthcare has evolved significantly, providing patients with improved access to services and information. However, the increased reliance on digital platforms also means that healthcare providers are more susceptible to DDoS attacks.
Online services have become a cornerstone of modern healthcare with patients using online portals to access their health records, book appointments, and interact with their healthcare providers. Consequently, the availability and reliability of these services are crucial to providing timely and effective healthcare.
A DDoS attack on a healthcare provider can have far-reaching consequences. It can disrupt access to health records, delay critical care, and potentially put lives at risk. Moreover, it can compromise patient data, resulting in a loss of trust and potential legal repercussions.
By investing in DDoS mitigation, healthcare providers can ensure continuous access to health records and services, protect sensitive patient data, and enhance patient trust and care.
Online gaming & gambling
Lastly, we have application layer attacks. These attacks mimic normal user behavior and target the weakest link in any network’s security — the application layer.
These kinds of attacks are often harder to detect as they operate on a level that doesn’t immediately overwhelm bandwidth or server resources, but rather slowly chips away at your system.
Tourism
The tourism industry relies heavily on online services, from providing personal information to facilitating bookings. Online services have revolutionized the tourism industry, making it easier for travelers to research destinations, compare prices, and make bookings. Any disruption to these services can lead to lost revenue and dissatisfied customers.
A DDoS attack can take reservation systems offline, leading to lost sales and potential damage to the brand’s reputation. These attacks can also disrupt other services such as customer support or payment processing.
With DDoS protection, tourism businesses can help ensure seamless access to booking and information services, protect customer data and online transactions, and uphold customer satisfaction and brand reputation.
Why protect business-critical information with Vercara’s DDoS mitigation
It’s not a question of if but when your online platforms will come under such an attack. And when they do, you’ll want to have the best DDoS protection in place.
Enter Vercara UltraDDoS Protect—one of the world’s largest dedicated, cloud-based, on-demand DDoS mitigation services. With a data scrubbing capacity of 15 TBPS, Vercara provides a robust shield for your online revenues, customer satisfaction, and brand reputation.
Thanks to its top-notch security operations manned 24/7 by senior-level DDoS mitigation professionals, Vercara can monitor and respond to threats flexibly, adapting defenses as attackers deploy different tactics from various vectors.
When attacked, Vercara’s solution redirects your traffic via DNS or BGP, cleaning it and forwarding only legitimate traffic to your infrastructure. This approach ensures that your services remain available to your customers even during an attack. Once the threat subsides, simply switch your DNS A records back to your original IPs.
DDoS attacks are a part of the internet landscape, but they don’t have to disrupt your business. With Vercara UltraDDoS Protect, you can ensure that your digital assets are safe and that your online business runs uninterrupted. Don’t wait until you’re under attack—get in touch with Vercara today and protect your online presence
Ready to safeguard your enterprise with the best-in-class DDoS mitigation? Book a demo today.