Our Cyber Threat Intelligence Team produces 2 monthly internal reports: one for UltraWAF and one for UltraDDoS Protect. These are derived from attack data to show the size, scope, and nature of the attacks that we manage across our customer base.
As we were writing the report for the month of April, we found a very interesting data anomaly: we reported more WAF and bot violations than we had HTTP and HTTPS requests across all our customers for the entire month.
This chart, part of our UltraWAF monthly report, shows the total WAF and bot violations as a percentage of HTTP requests. You can see that the percentage of violations exceeds 100% for April 17 and 18.

Normally, WAF violations are somewhere in the range of 20-25% of the total web requests, and bot violations are less than 5% of web requests. This graph was, as Alice in Wonderland says, “Curiouser and curiouser!”, so we absolutely had to go down that rabbit hole and see what we could find out.
It’s very common for a single HTTP/HTTPS request to generate multiple violations inside UltraWAF and Bot Management. We trigger this all the time using our WAF and bot honeypot configurations where we collect all the attacks against our target sites but do not block anything. However, the number of requests that match multiple countermeasures is usually a tiny percentage of overall violations that we see. For this to happen across all of our customers and all their sites, something significant must have happened.
Once we started to look at statistics on a per-customer basis, it didn’t take us long to find out the source of the anomaly. We had a single customer that was the target of a hacktivist DDoS campaign for April 17 and 18 and this activity dwarfed our usual attack volumes.
The target site’s traffic went from an average daily volume of approximately 1,305,000 web requests to a spike of almost 5.7 million web requests (an increase of 336%) on April 17 and 2.1 million requests (a 63.92% increase) on April 18. The target site also had a significant increase in daily WAF violations from an average of approximately 258,000 to an increase of over 56 million (an increase of 33,500%) on April 17 and an increase to over 56.9 million (an increase of 21,900%) on April 18. Regarding the site’s bot traffic, this site normally receives approximately 73,000 bots in a day but on April 17 that number grew to over 104 million (an increase of over 141,000%) and on April 18 the bot traffic was approximately 61 million (an increase of over 82,000%).

They also had a corresponding set of mitigations through UltraDDoS Protect during this time, so the WAF and bot violations represented the application layer traffic that was passed by the initial DDoS mitigations. We protected them against several waves of network DDoS traffic against a handful of target IP addresses on April 17 and 18 and mitigated a peak of 71.25Mbps and 88Kpps of DDoS traffic on April 18. On April 17, we mitigated 41Mbps and 50.5Kpps. For comparison, their normal daily peak is around 300Kbps and 2Kpps.
As far as the size of attacks that we’ve seen, this is far from being the largest. I consider a “respectable” attack to be larger than 5Gbps and the average attack that we see is around 8Gbps. We do track mega-attacks that are larger than 100Gbps. However, this attack against our customer was a relatively rare type of DDoS that uses both network/volumetric attacks and valid HTTP/HTTPS GET floods.
Our recommendations for protecting websites against hacktivist DDoS attacks with UltraWAF:
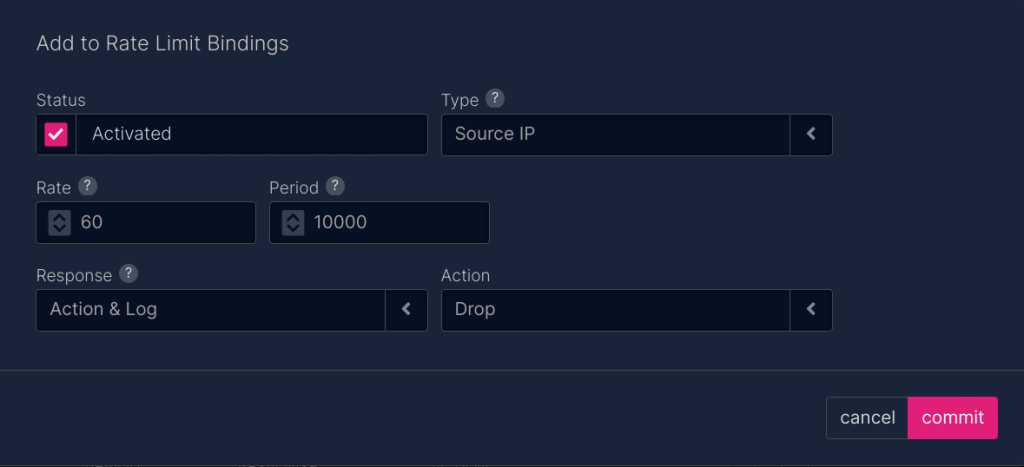
UltraWAF provides a lot of basic DDoS protections natively by having its Virtual IP pool protected by UltraDDoS Protect. Additionally, it drops all traffic for traffic that does not have a front-end configured. Set a basic set of rate controls against Source IP with an action of “drop” inside the Bot Profile tab.
In this example, the policy will block bots that send more than 60 web requests in a 10-second (10000 milliseconds) timeframe. That’s usually more than an individual web browser will send. You can test this in logging-only mode and then adjust the rate higher if necessary.
Enable IP Reputation controls inside the Bot Profile tab to drop traffic for “Botnets”, “DoS”, and “Scanners”.


Inside the Network Controls tab, proactively block countries under sanctions and be prepared to block additional countries as a quick policy change. We have seen a lot of hacktivist-related DDoS activity coming from Eastern European addresses, even when the protest is about a Western European or North American issue.
And lastly, hacktivists rarely limit themselves to just DDoS attacks. Enabling basic countermeasures for SQL Injection, Cross-Site Scripting, etc. in blocking mode can protect you against data breaches and defacements.
As demonstrated by these attacks, UltraWAF and UltraDDoS Protect are complementary solutions when it comes to complex DDoS attack campaigns like this that target hosting platforms, in the form of network blocks and datacenters, and flagship services such as interactive websites. Combined with the DDoS mitigation features of UltraDNS and our other security features and solutions, Vercara is more than capable of protecting your applications, services, and brand.
To learn more about how our suite of products can help secure your online experience, schedule a demo with our sales team.

