Of all the fundamental elements of the internet, the Domain Name System (DNS) is perhaps the most important. It allows internet users to locate and navigate online resources, including your organization’s homepage and online services, and makes the modern online experience possible. However, DNS’ vital importance makes it a frequent target for bad actors looking to disrupt the online services of organizations.
While a DNS solution is a critical first step in protecting your organization from DNS attacks, the next best way to defend your online resources is to stay up to date on the attack trends and patterns. Using data collected from our DNS solution, UltraDNS, our Security Operations Center (SOC) team has put together a monthly report to provide you with the latest insights and knowledge regarding DNS traffic.
To read the latest report, click here.
Table of Contents
Introduction
Vercara’s managed DNS services offer a variety of traffic management and steering options, enabling customers to manage and maintain a fast, reliable, and accurate global resolution for their digital properties. Our managed DNS solutions include customizable primary, secondary, or dual primary DNS services backed by two fully redundant networks for seamless service delivery. With comprehensive DNS management addressing modern challenges, including scalability, security, simplicity, cost efficiency, and compliance (https://vercara.com/managed-dns-service-provider).
This report summarizes Domain Name System (DNS) usage trends and attacks received by UltraDNS for March 2024. It is a recurring report highlighting monthly trends observed by our platform and analysts. This report is released as TLP:CLEAR except where noted.
Overall DNS usage trends and attack themes:
- UltraDNS receives a large volume of DNS queries for some of the top Internet properties, and as such, its traffic statistics reflect usages across the Internet in general.
- The IPv6 adoption can be inferred from corresponding query types and counts against each protocol.
- DNS supports both UDP 53 and via TLS over TCP 53 protocols with several tradeoffs in speed v/s integrity.
- DDoS attackers frequently target DNS servers because all other services depend on timely DNS resolutions.
- UltraDNS receives DDoS attacks directed at its customers. Vercara mitigates DDoS attacks against the UltraDNS platform as necessary to preserve the availability and performance of the platform for all customers.
- Attackers use DNS reconnaissance and enumeration tools like dnsenum to identify hostnames inside of a domain which they can then attack.
- NXDOMAIN traffic, where the domain or FQDN does not exist, is a reality for large authoritative DNS providers that impacts us and our customers in several ways.
- Some types of DNS Resource Records, such as HTTPS, are newer standards and are increasing in adoption.
Stats at a glance
Total Authoritative Queries: 3.84 trillion (7.77% increase from February 2024)
Percentage of queries using IPV6: 23% (10.36% increase in total count from February 2024)
Percentage of queries for AAAA (IPV6) records: 19.29% (8.96% increase in total count from February 2024)
Percentage of NOERR query answers: 80.50% (7.68% increase in total count from February 2024)
Percentage of NXDOMAIN query answers: 19.94% (8.34% increase in total count from February 2024)
Number of DDoS attacks against UltraDNS: 161
DNS statistics and trends
As a large, dedicated authoritative DNS service, UltraDNS hosts zone information for Top-Level Domains, some of the most popular second-level domains on the internet, and millions of small-usage domains. This also means that UltraDNS receives a high volume of DNS queries monthly and that this volume reflects overall usage of the Internet. March 2024 saw over 3.84 trillion DNS queries requested through the Vercara’s UltraDNS servers, this is a 7.77% increase from the previous month. There was an average of 123.89 billion authoritative queries per day, a 0.82% increase from the previous month.

DNS query type
Each DNS zone consists of Resource Records and record types. These are specified inside of each DNS query, and changes in their usage reflect the steady evolution of DNS and the Internet itself.
During the period of observation, the “A” record accounted for over 55.28% of queries, this represents that most DNS queries are conducted for IPv4 IP addresses. The “AAAA” (also known as “quad-A”) type was second with 19.29%, and it is expected that this percentage will grow over time as the IPv6 protocol continues to gain adoption. The “HTTPS” query type was the third most prevalent, with 6.72% of all DNS queries, and indicates that organizations/companies are adopting this newer type of Resource Record. The report also provides a detailed breakdown of other query types, including “NS” (Name Server) queries, “PTR” (Pointer) queries, and various others. Each of these query types serves a different purpose within DNS operations. For example, “NS” records, which help with delegating DNS zones, accounted for 6.00% of the queries, while “PTR” records, used for reverse DNS lookups, comprised 3.58%.
This thorough analysis of DNS query types provides insights into the technical operations of internet addressing and domain name resolution. It also reflects the broader trends in internet usage, security considerations, and the gradual shift towards newer protocols like IPv6. This highlights the critical role of DNS in enabling the functionality of the internet, supporting the transition towards more secure and robust network infrastructures, and adapting to the changing landscape of internet technology.

DNS response codes
Each DNS response includes a status code. The status code can be used to understand server health, client abuse, or other protocol anomalies.
For March 2024, the “No Error” response code was by far the most prevalent response code, with 80.50%. This is a strong indicator that most of the DNS queries are answered without issues and to gauge the overall health of the UltraDNS platform to answer queries at scale. The “NX Domain” response code was second in frequency with 19.94% and is used as an answer to queries for domains and FQDNs that do not exist. This could be the result of misconfigurations in the zone, DNS enumeration tools, or some kinds of DDoS traffic such as DNS water torture attacks. The “Refused” response code was third with 0.55%. This indicates malformed queries, policy enforcement on UltraDNS, or unauthorized attempts to access resources, reinforcing the importance of the per-query security controls built into UltraDNS. The SERVFAIL response code, ranking fourth with a frequency of 0.01%, typically indicates that the DNS resolver was unable to resolve the DNS query successfully. This failure can often be attributed to various issues, such as network errors, server misconfigurations, or operational faults within the DNS infrastructure, rather than solely to security controls like firewalls or intrusion prevention systems. While security mechanisms can contribute to such failures by blocking access to specific domains, SERVFAIL broadly signifies that the resolver encountered difficulties in the resolution process, encompassing a range of potential causes beyond security policies alone.

The blow chart shows the month-over-month change from February to March in response codes returned. For March 2024, the biggest change was in the Form Error response code with an increase of 284.18%. The second biggest change was in the Servfail response code with an increase of 32.60%.

Internet Protocol
UltraDNS listens to queries on two service ports, UDP 53 and TCP 53, and on 2 versions of IP addresses, IPV4 and IPV6. Usage of these 4 variations reflects capabilities and preferences built into recursive DNS servers that receive queries from end users.
IPv4 was used for 77.19% of queries, while IPv6 accounted for 22.81%. Most DNS queries were done via the User Datagram Protocol (UDP) with 99.38% and the Transmission Control Protocol (TCP) with 0.62%.

UltraDNS vs UltraDNS2
Vercara maintains and operates a separate DNS anycast resolution network called UltraDNS2 that provides diversity and redundancy across data centers, networks, and Network Operations Centers. UltraDNS2 is used by the largest, most popular domains and some TLDs.
For March 2024, UltraDNS2 accounted for 6.22% of total queries, while UltraDNS accounted for 93.78%.

Distributed Denial-of-Service (DDoS) attacks against UltraDNS
DNS is heavily targeted by DDoS attacks because all other services have a dependence on the availability of DNS to direct traffic to them. Vercara’s UltraDDoS Protect service was created initially to protect UltraDNS against DDoS attacks and was later expanded to protect customer networks.
In March 2024, Vercara observed and mitigated 161 DDoS attacks targeted against the UltraDNS platform, accounting for 2.55% of all observed DDoS attacks in March. The largest DDoS attack observed was 15.45 Gbps with over three thousand Packets-per-Second (pps) and lasted approximately eight minutes. The observed DDoS attacks were attacks that exceeded mitigation thresholds and did not include smaller DDoS attacks that were automatically mitigated and did not require a more advanced response.
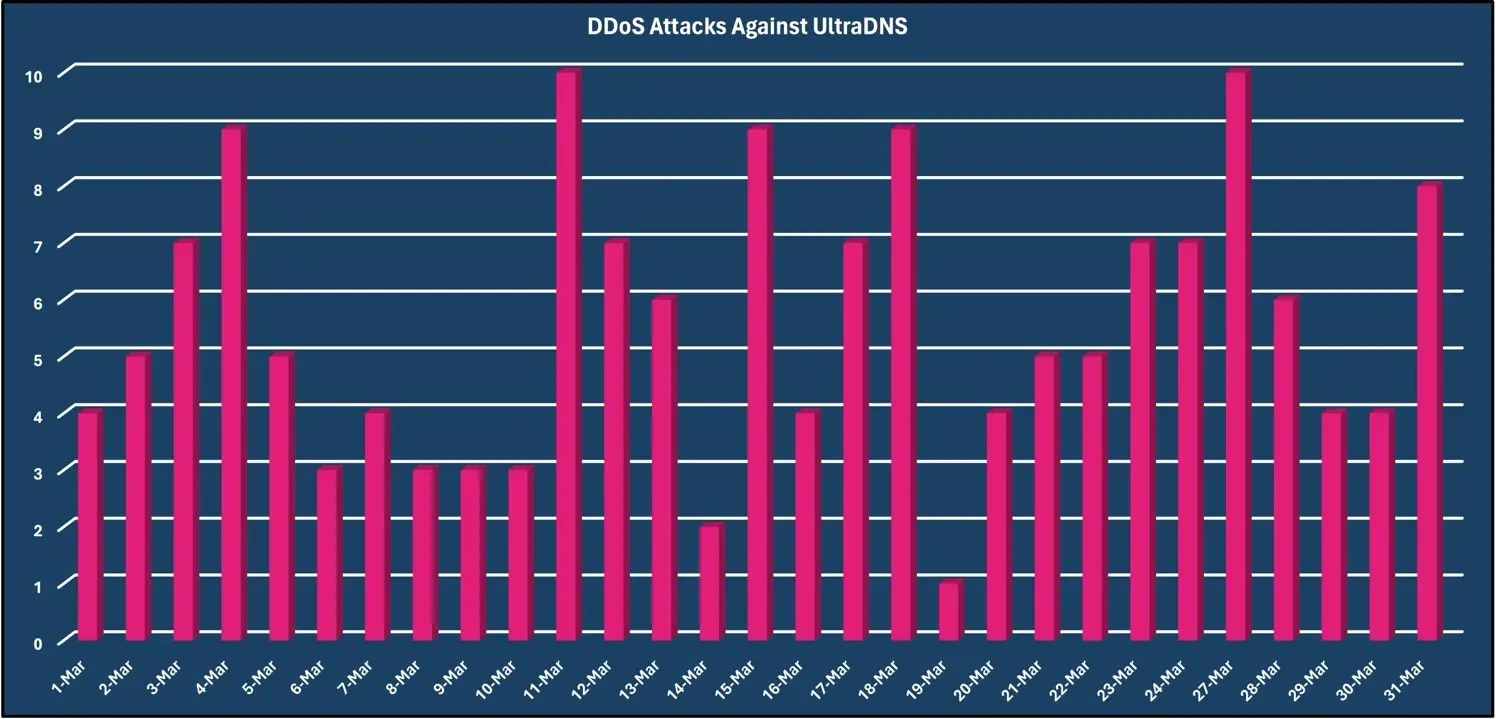
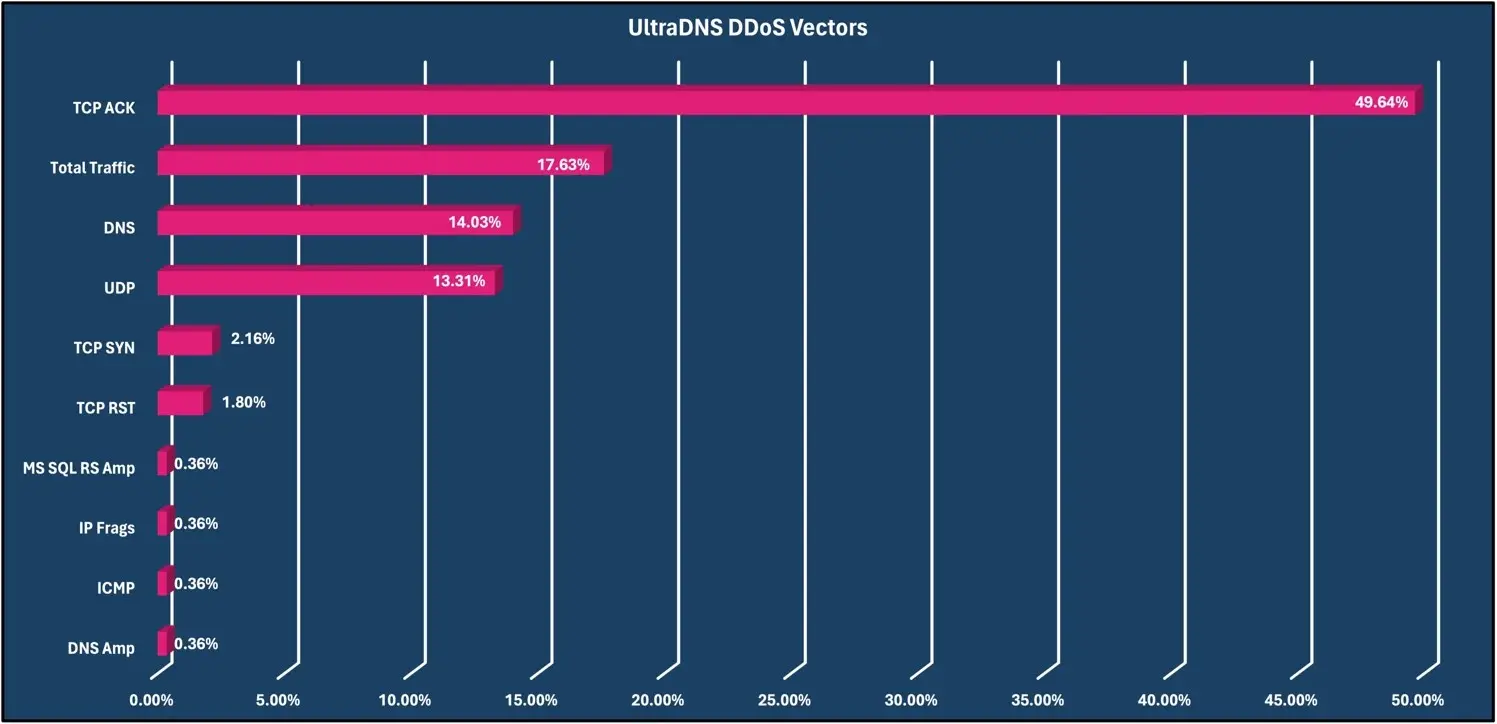
DDoS attacks can use a variety of ports and protocols to flood the target’s infrastructure regardless of the services that are exposed to the Internet. Because most DNS queries use the UDP variant, authoritative DNS servers are sometimes used for amplification attacks. And lastly, Vercara has been tracking the advent of “DNS Water Torture” attacks which send a massive volume of well-formed queries for non-existent FQDNs against a target domain to an authoritative DNS server or infrastructure with the intent to disrupt its services.
During this reporting period, the TCP ACK DDoS vector was the vector most used with 49.64%, with the Total Traffic vector being second with 17.63%.
DNS queries by country
DNS query source countries reflect usage across the internet but also the location of large network resolvers such as provided by ISPs (Internet Service Providers), datacenters, and Vercara’s own public DNS which is documented at https://vercara.com/ultra-dns-public. The large public recursive servers mostly use BGP anycast for their Points of Presence, which will be geolocated to the country where the operating company is located.
During this reporting period, the United States was observed generating the most DNS query traffic with 39.95%. The second country generating the most DNS query traffic was the United Kingdom with 4.27% and China was third with 3.37%.

This document is released as TLP: CLEAR. Traffic Light Protocol definitions and usage are maintained by the Forum of Incident Response and Security Teams at https://www.first.org/tlp/
About Vercara.
The world’s top brands depend on Vercara to safeguard their digital infrastructure and online presence. Vercara offers a suite of cloud-delivered services that are always secure, reliable, and available and enable global businesses to thrive online. UltraSecure protects organizations’ networks and applications against risks and downtime, ensuring that businesses and their customers enjoy exceptional and uninterrupted interactions all day, every day. Delivering the industry’s best performance and always-on service, Vercara’s mission-critical security portfolio provides best-in-class DNS, application, and network security, including DDoS, WAF, and Bot management services to its global 5000 customers and beyond.
To learn more about Vercara solutions, please visit our solutions overview page or contact us.




